Risk management plan
IT Risk Management Process
IT controls result from an effective, risk assessment process. Therefore, the ability to mitigate IT risks is dependent upon risk assessments. Senior management should identify, measure, control, and monitor technology to avoid risks that threaten the safety and soundness of an institution.
The institution should:
- Plan for use of technology
- Assess the risk associated with technology
- Decide how to implement the technology
- Establish a process to measure and monitor risk that is taken on
All organizations should have:
- An effective planning process that aligns IT and business objectives
- An ongoing risk assessment process that evaluates the environment and potential changes
- Technology implementation procedures that include appropriate controls
- Measurement and monitoring efforts that effectively identify ways to manage risk exposure
This process will typically require a higher level of formality in more complex institutions with major technology-related initiatives.
The risk identification and management process for technology-related risks is not complete without consideration of the overall IT environment in which the technology resides.
Management may need to consider risks associated with IT environments from two different perspectives:
- If the IT function is decentralized, and business units manage the risk, then management should coordinate risk management efforts through common organization-wide expectations.
- If the IT department is a centralized function that supports business lines across shared infrastructure, management should centralize their IT risk management efforts.
Risk Management Approach Primer
The risk-based approach to security control selection and specification considers effectiveness, efficiency, and constraints due to applicable laws, directives, executive orders, policies, standards, or regulations. The following activities related to managing organizational risk are paramount to an effective information security program and can be applied to both new and legacy information systems within the context of the system development life cycle and the organizational enterprise information technology architecture:
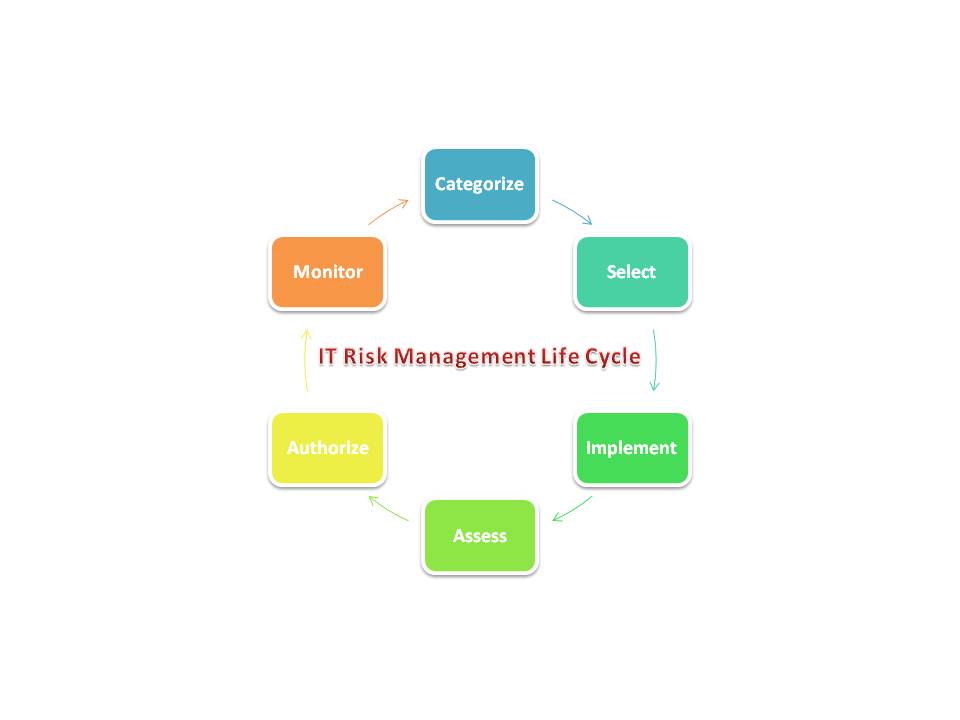
Categorize
- Categorize the information system and the information resident within that system based on impact.
Select
- Select an initial set of security controls for the information system based on the security categorization and the minimum security requirements defined; apply tailoring guidance as appropriate; and supplement the tailored baseline security controls based on an assessment of risk and local conditions including organization-specific security requirements, specific threat information, cost-benefit analyzes, or special circumstances.
Implement
- Implement the security controls in the information system.
Assess
- Assess the security controls using appropriate methods and procedures to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the system.
Authorize
- Authorize information system operation based upon a determination of the risk to organizational operations, organizational assets, or to individuals resulting from the operation of the information system and the decision that this risk is acceptable.
Monitor
- Monitor and assess selected security controls in the information system on a continuous basis including documenting changes to the system, conducting security impact analyzes of the associated changes, and reporting the security status of the system to appropriate organizational officials on a regular basis.