Uploads by Mdpeters
Jump to navigation
Jump to search
This special page shows all uploaded files.
| Date | Name | Thumbnail | Size | Description | Versions |
|---|---|---|---|---|---|
| 19:51, 13 January 2014 | Asset Management Standard.png (file) |  |
38 KB | 1 | |
| 19:40, 13 January 2014 | Asset Protection Standard(1).png (file) |  |
50 KB | 1 | |
| 19:40, 13 January 2014 | Asset Protection Standard(2).png (file) |  |
100 KB | 1 | |
| 19:41, 13 January 2014 | Asset Protection Standard(3).png (file) |  |
113 KB | 1 | |
| 19:41, 13 January 2014 | Asset Protection Standard(4).png (file) |  |
107 KB | 1 | |
| 19:42, 13 January 2014 | Asset Protection Standard(5).png (file) |  |
78 KB | 1 | |
| 19:42, 13 January 2014 | Asset Protection Standard(6).png (file) |  |
27 KB | 1 | |
| 19:40, 13 January 2014 | Asset Protection Standard.png (file) |  |
37 KB | 1 | |
| 20:10, 12 October 2014 | AuditMachine-AD2014.gif (file) |  |
81 KB | 1 | |
| 20:10, 15 January 2014 | Auditing Standard(1).png (file) |  |
50 KB | 1 | |
| 20:10, 15 January 2014 | Auditing Standard(2).png (file) |  |
76 KB | 1 | |
| 20:10, 15 January 2014 | Auditing Standard(3).png (file) |  |
59 KB | 1 | |
| 20:11, 15 January 2014 | Auditing Standard(4).png (file) |  |
64 KB | 1 | |
| 20:11, 15 January 2014 | Auditing Standard(5).png (file) |  |
110 KB | 1 | |
| 20:11, 15 January 2014 | Auditing Standard(6).png (file) |  |
60 KB | 1 | |
| 20:10, 15 January 2014 | Auditing Standard.png (file) |  |
36 KB | 1 | |
| 21:01, 15 January 2014 | Availability Protection Standard(1).png (file) |  |
50 KB | 1 | |
| 21:01, 15 January 2014 | Availability Protection Standard(2).png (file) |  |
83 KB | 1 | |
| 21:02, 15 January 2014 | Availability Protection Standard(3).png (file) |  |
76 KB | 1 | |
| 21:02, 15 January 2014 | Availability Protection Standard(4).png (file) | 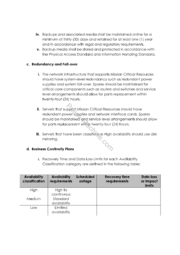 |
78 KB | 1 | |
| 21:02, 15 January 2014 | Availability Protection Standard(5).png (file) |  |
85 KB | 1 | |
| 21:03, 15 January 2014 | Availability Protection Standard(6).png (file) |  |
119 KB | 1 | |
| 21:03, 15 January 2014 | Availability Protection Standard(7).png (file) |  |
39 KB | 1 | |
| 21:01, 15 January 2014 | Availability Protection Standard.png (file) |  |
38 KB | 1 | |
| 21:56, 20 July 2012 | BCP-HORSE-2007053001.jpg (file) |  |
162 KB | 2 | |
| 10:39, 27 October 2012 | BCPLifecycle.gif (file) | 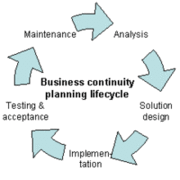 |
8 KB | 1 | |
| 18:11, 14 January 2014 | BYOD Acceptable Use Standard(1).png (file) |  |
50 KB | 1 | |
| 18:15, 14 January 2014 | BYOD Acceptable Use Standard(10).png (file) |  |
32 KB | 1 | |
| 18:12, 14 January 2014 | BYOD Acceptable Use Standard(2).png (file) |  |
99 KB | 1 | |
| 18:12, 14 January 2014 | BYOD Acceptable Use Standard(3).png (file) |  |
80 KB | 1 | |
| 18:12, 14 January 2014 | BYOD Acceptable Use Standard(4).png (file) |  |
77 KB | 1 | |
| 18:13, 14 January 2014 | BYOD Acceptable Use Standard(5).png (file) |  |
87 KB | 1 | |
| 18:13, 14 January 2014 | BYOD Acceptable Use Standard(6).png (file) |  |
85 KB | 1 | |
| 18:14, 14 January 2014 | BYOD Acceptable Use Standard(7).png (file) |  |
74 KB | 1 | |
| 18:14, 14 January 2014 | BYOD Acceptable Use Standard(8).png (file) |  |
76 KB | 1 | |
| 18:15, 14 January 2014 | BYOD Acceptable Use Standard(9).png (file) |  |
101 KB | 1 | |
| 18:11, 14 January 2014 | BYOD Acceptable Use Standard.png (file) |  |
38 KB | 1 | |
| 10:00, 28 July 2012 | BackupSystemAudit.txt (file) | 22 KB | 2 | ||
| 21:12, 29 July 2012 | BeKnown.jpg (file) |  |
16 KB | 1 | |
| 11:19, 4 July 2015 | Blacklock.png (file) |  |
3 KB | 1 | |
| 11:21, 4 July 2015 | Bluelock.png (file) |  |
3 KB | 3 | |
| 14:59, 23 July 2012 | Business-Case-for-Computer-Forensics.pdf (file) |  |
147 KB | 2 | |
| 21:05, 19 July 2012 | CFLC-tn.jpg (file) |  |
15 KB | 2 | |
| 09:50, 28 July 2012 | CIRCULAR-NO-A-130.pdf (file) |  |
92 KB | 2 | |
| 23:52, 21 July 2012 | Cism-mdp-20081.jpg (file) |  |
584 KB | 2 | |
| 09:51, 28 July 2012 | Cissp.jpg (file) |  |
2 KB | 2 | |
| 17:20, 21 August 2012 | Classes10.png (file) |  |
11 KB | 1 | |
| 16:48, 23 July 2012 | Computer-Forensics-Laboratory.pdf (file) |  |
97 KB | 2 | |
| 16:53, 23 July 2012 | Computer-Forensics-Today.pdf (file) |  |
77 KB | 2 | |
| 14:57, 23 July 2012 | Configuration-management-security.pdf (file) |  |
167 KB | 2 |