Security Management:: Difference between revisions
| (28 intermediate revisions by 2 users not shown) | |||
| Line 20: | Line 20: | ||
The output gives justification information to the realization of the SLAs and a report with deviations from the requirements. | The output gives justification information to the realization of the SLAs and a report with deviations from the requirements. | ||
The Security Management Process has relations with almost all other ITIL-processes. However, in this particular section the most obvious relations will be the relations to the [[Service Level Management]] process, the [[Incident | The Security Management Process has relations with almost all other ITIL-processes. However, in this particular section the most obvious relations will be the relations to the [[Service_Level_Management: | Service Level Management]] process, the [[Incident_Management: | Incident Management]] process and the [[Change_Management: | Change Management]] process. | ||
== The Security Management Process == | == The Security Management Process == | ||
| Line 49: | Line 49: | ||
|- | |- | ||
| Control | | Control | ||
| Implement | | Implement Policies | ||
| This process outlines the specific requirements and rules that have to be met in order to implement security management. The process ends with POLICY STATEMENTS. | | This process outlines the specific requirements and rules that have to be met in order to implement security management. The process ends with POLICY STATEMENTS. | ||
|- | |- | ||
| Control | | Control | ||
| Setup the | | Setup the Security Organization | ||
| This process sets up the organizations for information security. For example in this process the structure the responsibilities are set up. This process ends with SECURITY MANAGEMENT FRAMEWORK. | | This process sets up the organizations for information security. For example in this process the structure the responsibilities are set up. This process ends with SECURITY MANAGEMENT FRAMEWORK. | ||
|- | |- | ||
| Line 102: | Line 102: | ||
===Plan=== | ===Plan=== | ||
The Plan sub-process contains activities that in cooperation with the [[Service Level Management]] lead to the (information) Security section in the SLA. Furthermore, the Plan sub-process contains activities that are related to the underpinning contracts which are specific for (information) security. | The Plan sub-process contains activities that in cooperation with the [[Service_Level_Management: | Service Level Management]] lead to the (information) Security section in the SLA. Furthermore, the Plan sub-process contains activities that are related to the underpinning contracts which are specific for (information) security.<br> | ||
<br> | |||
In the Plan sub-process the goals formulated in the SLA are specified in the form of Operational Level Agreements (OLA). These OLA’s can be defined as security plans for a specific internal organization entity of the service provider. | In the Plan sub-process the goals formulated in the SLA are specified in the form of Operational Level Agreements (OLA). These OLA’s can be defined as security plans for a specific internal organization entity of the service provider.<br> | ||
<br> | |||
Besides the input of the SLA, the Plan sub-process also works with the policy statements of the service provider itself. As said earlier these policy statements are defined in the control sub-process. | Besides the input of the SLA, the Plan sub-process also works with the policy statements of the service provider itself. As said earlier these policy statements are defined in the control sub-process.<br> | ||
<br> | |||
The Operational Level Agreements for information security are setup and implemented based on the ITIL process. This means that there has to be cooperation with other ITIL processes. For example if the security management wishes to change the IT infrastructure in order to achieve maximum security, these changes will only be done through the [[Change Management]] process. The Security Management will deliver the input (Request for change) for this change. The change Manager is responsible for the Change Management Process itself. | The Operational Level Agreements for information security are setup and implemented based on the ITIL process. This means that there has to be cooperation with other ITIL processes. For example if the security management wishes to change the IT infrastructure in order to achieve maximum security, these changes will only be done through the [[Change_Management: | Change Management]] process. The Security Management will deliver the input (Request for change) for this change. The change Manager is responsible for the Change Management Process itself.<br> | ||
<br> | |||
'''TABLE 2.3.1: Activity Plan the (Sub) Activities and their Definition.''' | '''TABLE 2.3.1: Activity Plan the (Sub) Activities and their Definition.''' | ||
<br> | <br> | ||
| Line 138: | Line 138: | ||
As you can see the plan sub-process consists of a combination of unordered and ordered (sub) activities. Furthermore, it is noticeable that the sub-process contains three complex activities which are all closed activities and one standard activity.<br> | As you can see the plan sub-process consists of a combination of unordered and ordered (sub) activities. Furthermore, it is noticeable that the sub-process contains three complex activities which are all closed activities and one standard activity.<br> | ||
<br> | <br> | ||
Table 2.2.1 consists of concepts that are created or adjusted during the plan sub-process. The table also gives a definition of these concepts.<br> | '''Table 2.2.1''' consists of concepts that are created or adjusted during the plan sub-process. The table also gives a definition of these concepts.<br> | ||
<br> | <br> | ||
'''TABLE 2.2.1: Sub Activities and Description Plan Sub-Process ITIL Security Management.'''<br> | '''TABLE 2.2.1: Sub Activities and Description Plan Sub-Process ITIL Security Management.'''<br> | ||
| Line 159: | Line 159: | ||
|} | |} | ||
<br> | <br> | ||
Table 2.2.2: Concept and definition Plan sub-process Security management.<br> | '''Table 2.2.2:''' Concept and definition Plan sub-process Security management.<br> | ||
<br> | |||
Just as the Control sub-process the Plan sub-process is modeled using the meta-modeling technique. The left side of '''figure 2.2.1''' is the meta-data model of the Plan sub-process.<br> | |||
<br> | |||
The plan rectangle is an open (complex) concept which has an aggregation type of relationship with two closed (complex) concepts and one standard concept. The two closed concepts are not expanded in this particular context.<br> | |||
<br> | |||
The following picture (figure 2.2.1) is the process-data diagram of the Plan sub-process. This picture shows the integration of the two models. The dotted arrows indicate which concepts are created or adjusted in the corresponding activities of the Plan sub-process.<br> | |||
<br> | |||
[[Image:Plan_process_data_model.jpg]]<br> | |||
<br> | |||
'''Figure 2.2.1:''' Process-data Model Plan sub-process | |||
<br> | <br> | ||
===Implementation=== | ===Implementation=== | ||
| Line 186: | Line 187: | ||
| Implement | | Implement | ||
| Classify and managing of IT applications. | | Classify and managing of IT applications. | ||
| Process of formally grouping configuration items by type, e.g., software, hardware, documentation, environment, application. Process of formally identifying changes by type e.g., project scope change request, validation change request, infrastructure change request this process leads to | | Process of formally grouping configuration items by type, e.g., software, hardware, documentation, environment, application. Process of formally identifying changes by type e.g., project scope change request, validation change request, infrastructure change request this process leads to Asset Classification and Control Documents. | ||
|- | |- | ||
| Implement | | Implement | ||
| Line 205: | Line 206: | ||
|} | |} | ||
<br> | <br> | ||
The left side of figure 2.3.1 is the meta-process model of the Implementation phase. The four labels with a black shadow mean that these activities are closed concepts and they are not expanded in this context. It is also noticeable that there are no arrows connecting these four activities this means that these activities are unordered and the reporting will be carried out after the completion of | The left side of figure 2.3.1 is the meta-process model of the Implementation phase. The four labels with a black shadow mean that these activities are closed concepts and they are not expanded in this context. It is also noticeable that there are no arrows connecting these four activities this means that these activities are unordered and the reporting will be carried out after the completion of all four activities.<br> | ||
<br> | <br> | ||
During the implementation phase there are a number of concepts that are created and or adjusted. See table 2.3.2 for an overview of the most common concepts and their description.<br> | During the implementation phase there are a number of concepts that are created and or adjusted. See table 2.3.2 for an overview of the most common concepts and their description.<br> | ||
| Line 218: | Line 219: | ||
| Accomplished security management according to the SECURITY MANAGEMENT PLAN. | | Accomplished security management according to the SECURITY MANAGEMENT PLAN. | ||
|- | |- | ||
| | | Asset Classification and Control Documents | ||
| A comprehensive inventory of assets with responsibility assigned to ensure that effective security protection is maintained. | | A comprehensive inventory of assets with responsibility assigned to ensure that effective security protection is maintained. | ||
|- | |- | ||
| Line 239: | Line 240: | ||
[[Image:Implementation_process_data_model.jpg]]<br> | [[Image:Implementation_process_data_model.jpg]]<br> | ||
<br> | <br> | ||
Figure 2.3.1: Process-data model Implementation sub-process<br> | '''Figure 2.3.1:''' Process-data model Implementation sub-process<br> | ||
<br> | <br> | ||
===Evaluation=== | ===Evaluation=== | ||
The evaluation of the implementation and the plans is very important. The evaluation is necessary to measure the success of the implementation and the Security plans. The evaluation is also very important for the clients (and possibly third parties). The results of the Evaluation sub-process are used to maintain the agreed measures and the implementation itself. Evaluation results can lead to new requirements and so lead to a | The evaluation of the implementation and the plans is very important. The evaluation is necessary to measure the success of the implementation and the Security plans. The evaluation is also very important for the clients (and possibly third parties). The results of the Evaluation sub-process are used to maintain the agreed measures and the implementation itself. Evaluation results can lead to new requirements and so lead to a request for change. The request for change is then defined and it is then send to the Change Management process.<br> | ||
<br> | |||
Mainly there are three sorts of evaluation; the Self assessment; internal audit, and external audit. | Mainly there are three sorts of evaluation; the Self assessment; internal audit, and external audit.<br> | ||
<br> | |||
The self assessment is mainly carried out in the organization of the processes. The internal audits are carried out by internal IT-auditors and the external audits are carried out by external independent IT-auditors. Besides, the evaluations already mentioned an evaluation based on the communicated security incidents will also take place. The most important activities for this evaluation are the security monitoring of IT-systems; verify if the security legislation and the implementation of the security plans are complied; trace and react to undesirable use of the IT-supplies. | The self assessment is mainly carried out in the organization of the processes. The internal audits are carried out by internal IT-auditors and the external audits are carried out by external independent IT-auditors. Besides, the evaluations already mentioned an evaluation based on the communicated security incidents will also take place. The most important activities for this evaluation are the security monitoring of IT-systems; verify if the security legislation and the implementation of the security plans are complied; trace and react to undesirable use of the IT-supplies.<br> | ||
<br> | |||
The activities that take place in the evaluation sub-process are summed up in the following table (Table 2.4.1). The table contains the name of the (sub) activity and a short definition of the activity. | The activities that take place in the evaluation sub-process are summed up in the following table (Table 2.4.1). The table contains the name of the (sub) activity and a short definition of the activity.<br> | ||
<br> | |||
'''TABLE 2.4.1: Sub-Activities and Descriptions Evaluation Sub-Process ITIL Security Management.'''<br> | |||
'''TABLE 2.4.1: Sub-Activities and Descriptions Evaluation Sub-Process ITIL Security Management.''' | |||
<br> | <br> | ||
{| id="table1" width="100%" border="1" | {| id="table1" width="100%" border="1" | ||
| Line 261: | Line 261: | ||
|- | |- | ||
| Evaluate | | Evaluate | ||
| Self | | Self Assessment. | ||
| In this process an examination of the implemented security agreements is done by the organization of the process it self. The result of this process is Self Assessment Documents. | | In this process an examination of the implemented security agreements is done by the organization of the process it self. The result of this process is Self Assessment Documents. | ||
|- | |- | ||
| Line 269: | Line 269: | ||
|- | |- | ||
| Evaluate | | Evaluate | ||
| External | | External Audit. | ||
| In this process an examination of the implemented security agreements is done by an external EDP auditor. The result of this process is External Audit. | | In this process an examination of the implemented security agreements is done by an external EDP auditor. The result of this process is External Audit. | ||
|- | |- | ||
| Line 285: | Line 285: | ||
Figure 2.4.1: Process-data model Evaluation sub-process<br> | Figure 2.4.1: Process-data model Evaluation sub-process<br> | ||
<br> | <br> | ||
The process-data diagram illustrated in the figure 2.4.1 consists of a meta-process model and a meta-data model. The Evaluation sub-process was modeled using the meta-modeling technique. The dotted arrows running from the meta-process diagram (left) to the meta-data diagram (right) indicate which concepts are created | The process-data diagram illustrated in the figure 2.4.1 consists of a meta-process model and a meta-data model. The Evaluation sub-process was modeled using the meta-modeling technique. The dotted arrows running from the meta-process diagram (left) to the meta-data diagram (right) indicate which concepts are created or adjusted in the corresponding activities. All of the activities in the evaluation phase are standard activities. For a short description of the Evaluation phase concepts see Table 2.4.2 where the concepts are listed and defined.<br> | ||
<br> | <br> | ||
'''TABLE 2.4.2: Concept and Definition Evaluation Sub-Process Security Management.'''<br> | '''TABLE 2.4.2: Concept and Definition Evaluation Sub-Process Security Management.'''<br> | ||
| Line 294: | Line 294: | ||
|- | |- | ||
| Evaluation | | Evaluation | ||
| | | Evaluate or check implementation. | ||
|- | |- | ||
| Results | | Results | ||
| Line 315: | Line 315: | ||
===Maintenance=== | ===Maintenance=== | ||
It is necessary for the security to be maintained. Because of changes in the IT-infrastructure and changes in the organization itself security risks are bound to change over time. The maintenance of the security concerns both the maintenance of the security section of the service level agreements and the more detailed security plans. | It is necessary for the security to be maintained. Because of changes in the IT-infrastructure and changes in the organization itself security risks are bound to change over time. The maintenance of the security concerns both the maintenance of the security section of the service level agreements and the more detailed security plans.<br> | ||
<br> | |||
The maintenance is based on the results of the Evaluation sub-process and insight in the changing risks. These activities will only produce proposals. The proposals serve as inputs for the plan sub-process and will go through the whole cycle or the proposals can be taken in the maintenance of the service level agreements. In both cases the proposals could lead to activities in the action plan. The actual changes will be carried by the Change Management process. | The maintenance is based on the results of the ''Evaluation'' sub-process and insight in the changing risks. These activities will only produce proposals. The proposals serve as inputs for the plan sub-process and will go through the whole cycle or the proposals can be taken in the maintenance of the service level agreements. In both cases the proposals could lead to activities in the action plan. The actual changes will be carried by the [[Change_Management: | Change Management]] process.<br> | ||
<br> | |||
The activities that take place in the maintain sub-process are summed up in the following table (Table 2.5.1). The table contains the name of the (sub) activity and a short definition of the activity. | The activities that take place in the maintain sub-process are summed up in the following table (Table 2.5.1). The table contains the name of the (sub) activity and a short definition of the activity.<br> | ||
<br> | |||
< | '''TABLE 2.5.1: Sub-Activities and descriptions Maintenance sub-process ITIL Security Management.'''<br> | ||
<br> | |||
{| id="table1" width="100%" border="1" | |||
| bgcolor="#C0C0C0" | '''Activities''' | |||
| bgcolor="#C0C0C0" | '''Sub-Activities''' | |||
| bgcolor="#C0C0C0" | '''Description''' | |||
|- | |||
| Maintain | |||
| Maintenance of service level agreements. | |||
| This is a process to keep the service level agreements in proper condition. The process ends with Maintained Service Level Agreements. | |||
|- | |||
| Maintain | |||
| Maintenance of operational level agreements. | |||
| This is a process to keep the operational level agreements in proper condition. The process ends with Maintained Operational Level Agreement. | |||
|- | |||
| Maintain | |||
| Request for change to SLA or OLA. | |||
| Request for a change to the SLA and or OLA is formulated. This process ends with a Request For Change. | |||
|- | |||
| Maintain | |||
| Reporting. | |||
| In this process the whole maintain implemented security policies process is documented in a specific way. This process ends with Reports. | |||
|} | |||
<br> | |||
Figure 2.5.1 is the process-data diagram of the implementation sub-process. This picture shows the integration of the meta-process model (left) and the meta-data model (right). The dotted arrows indicate which concepts are created or adjusted in the activities of the implementation phase.<br> | |||
<br> | |||
[[Image:Maintenance_process_data_model.jpg]]<br> | |||
<br> | |||
Figure 2.5.1: Process-data model Maintenance sub-process.<br> | |||
<br> | |||
The maintenance sub-process starts with the maintenance of the service level agreements and the maintenance of the operational level agreements. After these activities take place (in no particular order) and there is a request for a change the request for change activity will take place and after the request for change activity is concluded the reporting activity starts. If there is no request for a change then the reporting activity will start directly after the first two activities. The concepts in the meta-data model are created or adjusted during the maintenance phase. For a list of the concepts and their definition take a look at table 2.5.2.<br> | |||
<br> | |||
'''TABLE 2.5.2: Concept and Definition Plan Sub-Process Security Management.'''<br> | |||
<br> | |||
{| id="table1" width="100%" border="1" | |||
| bgcolor="#C0C0C0" | '''Concept''' | |||
| bgcolor="#C0C0C0" | '''Description''' | |||
|- | |||
| Maintenance Documents | |||
| Agreements kept in proper condition. | |||
|- | |||
| Maintained Service Level Agreements | |||
| Service Level Agreements(security paragraph) kept in proper condition. | |||
|- | |||
| Maintained Operational Level Agreements | |||
| Operational Level Agreements kept in proper condition. | |||
|- | |||
| Request For Change | |||
| Form or electronic process used to record details of a request for a change to the SLA or the OLA. | |||
|} | |||
<br> | |||
<br | |||
===Complete process-data model=== | ===Complete process-data model=== | ||
The following picture shows the complete process-data model of the Security Management process. This means that the complete meta-process model and the complete meta-data model and the integrations of the two models of the Security Management process are shown. | The following picture shows the complete process-data model of the Security Management process. This means that the complete meta-process model and the complete meta-data model and the integrations of the two models of the Security Management process are shown.<br> | ||
<br> | |||
[[Image:Process_data_model_security_management.jpg]] | [[Image:Process_data_model_security_management.jpg]]<br> | ||
<br> | |||
Figure 2.6.1: Process- | Figure 2.6.1: Process-Data Model Security Management Process.<br> | ||
<br> | |||
== Relations with other ITIL processes == | == Relations with other ITIL processes == | ||
The security Management Process, as stated in the introduction, has relations with almost al other ITIL-processes. These processes are: | The security Management Process, as stated in the introduction, has relations with almost al other ITIL-processes.<br> | ||
<br> | |||
* | '''These processes are:'''<br> | ||
<br> | |||
* | :* [[IT Customer Relationship Management]] | ||
* | :* [[Service_Level_Management: | Service Level Management]] | ||
* | :* [[Availability_Management: | Availability Management]] | ||
* | :* [[Capacity_Management: | Capacity Management]] | ||
:* [[Continuity_Management: | IT Service Continuity Management]] | |||
* | :* [[Configuration_Management: | Configuration Management]] | ||
* | :* [[Release Management: | Release Management]] | ||
:* [[Incident_Management: | Incident Management & Service Desk]]; See also: [[Sample_Incident_Response_Standard: | Sample Incident Response Standard]] | |||
:* [[Problem_Management: | Problem Management]] | |||
Within these processes there are a couple of activities concerning security that have to take place. These activities are done as required. The concerning process and its process manager are responsible for these activities. However, the Security Management will give indications to the concerning process on how these (security specific) activities should be structured. | :* [[Change_Management: | Change Management]] | ||
<br> | |||
Within these processes there are a couple of activities concerning security that have to take place. These activities are done as required. The concerning process and its process manager are responsible for these activities. However, the Security Management will give indications to the concerning process on how these (security specific) activities should be structured.<br> | |||
<br> | |||
== Example == | == Example == | ||
'''[[Media:Developmental Electronic Mail Acceptable Usage Standard.pdf | Email Policy]]'''.<br> | |||
<br> | |||
The use of internal e-mail in an organization has a lot of security risks. So if an organization chooses to use e-mail as a means of communication, it is highly needed that the organization implements a well thought e-mail security plan/policies. In this example the ITIL security Management approach is used to implement e-mail policies in an organization. | The use of internal e-mail in an organization has a lot of security risks. So if an organization chooses to use e-mail as a means of communication, it is highly needed that the organization implements a well thought e-mail security plan/policies. In this example the ITIL security Management approach is used to implement e-mail policies in an organization.<br> | ||
<br> | |||
First of the Security management team is formed and the guidelines, of how the process should be carried out, are formulated and made clear to all employees and provider concerned. These actions are carried out in the Control phase of the Security Management process. | First of the Security management team is formed and the guidelines, of how the process should be carried out, are formulated and made clear to all employees and provider concerned. These actions are carried out in the Control phase of the Security Management process.<br> | ||
<br> | |||
The next step in to process to implement e-mail policies is the Planning. In the Plan phase of the process the policies are formulated. Besides the policies that are already written in the Service Level Agreements the policies that are specific for the e-mail security are formulated and added to the service level agreements. At the end of this phase the entire plan is formulated and is ready to be implemented. | The next step in to process to implement e-mail policies is the Planning. In the Plan phase of the process the policies are formulated. Besides the policies that are already written in the Service Level Agreements the policies that are specific for the e-mail security are formulated and added to the service level agreements. At the end of this phase the entire plan is formulated and is ready to be implemented.<br> | ||
<br> | |||
The following phase in the process is the actual implementation of the e-mail policies. The implementation is done according to the plan which was formulated in the preceding phase (Plan phase). | The following phase in the process is the actual implementation of the e-mail policies. The implementation is done according to the plan which was formulated in the preceding phase (Plan phase).<br> | ||
<br> | |||
After the actual implementation the e-mail policies will be evaluated. In order to evaluate the implemented policies the organization will perform; | After the actual implementation the e-mail policies will be evaluated. In order to evaluate the implemented policies the organization will perform;<br> | ||
<br> | |||
The last phase is the maintenance phase. In the maintenance phase the implemented e-mail policies are maintained. The organization now knows which policies are properly implemented and are properly followed and, which policies need more work in order to help the security plan of the organization and, if there are new policies that have to be implemented. At the end of this process the Request for change are formulated (if needed) and the e-mail policies are properly maintained. | The last phase is the maintenance phase. In the maintenance phase the implemented e-mail policies are maintained. The organization now knows which policies are properly implemented and are properly followed and, which policies need more work in order to help the security plan of the organization and, if there are new policies that have to be implemented. At the end of this process the Request for change are formulated (if needed) and the e-mail policies are properly maintained.<br> | ||
<br> | |||
In order for the organization to keep its security plan up-to-date the organization will have to perform the security management process continuously. There is no end to this process an organization can always better its security. | In order for the organization to keep its security plan up-to-date the organization will have to perform the security management process continuously. There is no end to this process an organization can always better its security.<br> | ||
<br> | |||
The following picture gives an overview of the entire process of the | The following picture gives an overview of the entire process of the [[Media:Developmental Electronic Mail Acceptable Usage Standard.pdf | Email Policy]].<br> | ||
<br> | |||
== References == | == References == | ||
Latest revision as of 14:10, 27 February 2009
Security Management
The ITIL-process Security Management describes the structured fitting of information security in the management organization. ITIL Security Management is based on the code of practice for information security management also known as ISO/IEC 17799.
A basic concept of the Security Management is the information security. The primary goal of information security is to guarantee safety of the information. Safety is to be protected against risks. Security is the means to be safe against risks. When protecting information it is the value of the information that has to be protected. These values are stipulated by the confidentiality, integrity and availability. Inferred aspects are privacy, anonymity and verifiability.
The current move towards ISO/IEC 27001 may require some revision to the ITIL Security Management best practices which are often claimed to be rich in content for physical security but weak in areas such as software and or application security and logical security in the ICT infrastructure.
The ITIL Security Management Process describes the structured fitting of security in the management organization. ITIL Security Management is based on the Code of practice for information security management also known as ISO/IEC 17799.
A basic concept of Security Management is information security. The primary goal of information security is to guarantee safety of information. When protecting information it is the value of the information that has to be protected. These values are stipulated by the confidentiality, integrity and availability. Inferred aspects are privacy, anonymity and verifiability.
The goal of the Security Management is split up in two parts:
- The realization of the security requirements defined in the Service Level Agreement (SLA) and other external requirements which are specified in underpinning contracts, legislation and possible internal or external imposed policies.
- The realization of a basic level of security. This is necessary to guarantee the continuity of the management organization. This is also necessary in order to reach a simplified Service Level Management for the information security, as it happens to be easier to manage a limited number of SLAs as it is to manage a large number of SLAs.
The input of the Security Management process is formed by the SLAs with the specified security requirements, legislation documents (if applicable) and other (external) underpinning contracts. These requirements can also act as Key Performance Indicator (KPIs) which can be used for the process management and for the justification of the results of the Security Management process.
The output gives justification information to the realization of the SLAs and a report with deviations from the requirements.
The Security Management Process has relations with almost all other ITIL-processes. However, in this particular section the most obvious relations will be the relations to the Service Level Management process, the Incident Management process and the Change Management process.
The Security Management Process
The Security Management Process consists of activities that are carried out by the Security Management itself or activities that are controlled by the Security Management.
Because organizations and their information systems constantly change. The activities within the Security Management Process must be revised continuously, in order to stay up-to-date and effective. Security Management is a continuous process and it can be compared to the Quality Circle of Demming (Plan, Do, Check and Act).
The inputs are the requirements which are formed by the clients. The requirements are translated into security services, security quality that needs to be provided in the security section of the Service Level Agreements. As you can see in the picture there are arrows going both ways; from the client to the SLA; from the SLA to the client and from the SLA to the plan sub-process; from the plan sub-process to the SLA. This means that both the client and the plan sub-process have inputs in the SLA and the SLA is an input for both the client and the process. The provider then develops the security plans for his/hers organization. These security plans contain the security policies and the Operational Level Agreements. The security plans (Plan) are then implemented (Do) and the implementation is then evaluated (Check). After the evaluation the both the plans and the implementation of the plan are maintained (Act).
The activities, results and or products and the process are documented. External reports are written and sent to the clients. The clients are then able to adapt their requirements based on the information received through the reports. Furthermore, the service provider can adjust their plan or the implementation based on their findings in order to satisfy all the requirements stated in the SLA (including new requirements).
Control
The first activity in the Security Management Process is the “Control” sub-process. The Control sub-process organizes and manages the security Management process itself. The Control sub-process defines the processes, the allocation of responsibility the policy statements and the management framework.
The Security management framework defines the sub-processes for: the development of security plans, the implementation of the security plans, the evaluation and how the results of the evaluations are translated into action plans. Furthermore, the management framework defines how should be reported to clients.
The activities that take place in the Control Process are summed up in Table 2.1.1. Table 2.1.1 contains the name of the (sub) activity and a short definition of the activity.
TABLE 2.1.1: (Sub) activities and descriptions Control sub-process ITIL Security Management.
| Activities | Sub-Activities | Descriptions |
| Control | Implement Policies | This process outlines the specific requirements and rules that have to be met in order to implement security management. The process ends with POLICY STATEMENTS. |
| Control | Setup the Security Organization | This process sets up the organizations for information security. For example in this process the structure the responsibilities are set up. This process ends with SECURITY MANAGEMENT FRAMEWORK. |
| Control | Reporting | In this process the whole targeting process is documented in a specific way. This process ends with REPORTS. |
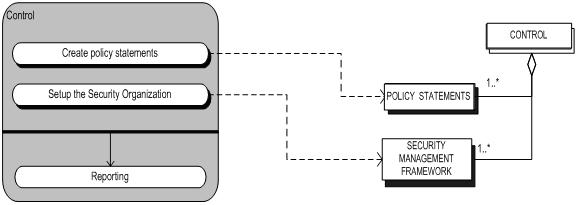
The meta-modeling technique was used in order to model the activities of the control sub-process. The following figure (figure 2-1) is the meta-process model of the control sub-process. It is based on a UML activity diagram and it gives an overview of the activities of the Control sub-process. The grey rectangle represents the control sub-process and the smaller beam shapes inside of the grey rectangle represent the activities that take place inside the control sub-process. The beams with a black shadow indicate that the activity is a closed (complex) activity. This means that the activity consists of a collection of (sub) activities but these activities are not expanded because they are not relevant in this particular context. The white beam without shadow indicates that the reporting activity is a standard activity. This means that reporting does not contain (sub) activities.
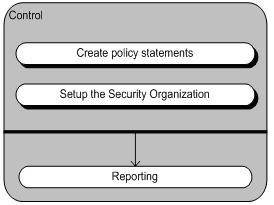
Furthermore, it is noticeable that the first two activities are not linked with an arrow and that there is a black stripe with an arrow leading to the reporting activity. This means that the two first activities are not sequential. They are unordered activities and after these two activities have taken place the reporting activity will sequentially follow.
TABLE 2.1.2: Concept Definition Table.
| Concept | Description (source) |
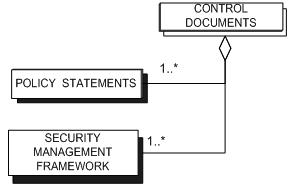
| Control Documents | CONTROL is a description of how SECURITY MANAGEMENT will be organized and how it will be managed. |
| Policy Statements | POLICY STATEMENTS are documents that outlines specific requirements or rules that must be met. In the information security realm, policies are usually point-specific, covering a single area. For example, an “Acceptable Use” policy would cover the rules and regulations for appropriate use of the computing facilities. |
| Security Management Framework | SECURITY MANAGEMENT FRAMEWORK is An established management framework to initiate and control the implementation of information security within your organization and to manage ongoing information security provision. |
The meta-data model of the control sub-process is based on a UML class diagram.
Figure 2.1.2 is the meta-data model of the control sub-process.
Figure 2.1.2: Meta-process model control sub-process
The CONTROL rectangle with a white shadow is an open complex concept. This means that the CONTROL rectangle consists of a collection of (sub) concepts and these concepts are expanded in this particular context.
The following picture (figure 2.1.3) is the process-data model of the control sub-process. This picture shows the integration of the two models. The dotted arrows indicate which concepts are created or adjusted in the corresponding activities.
Figure 2.1.3: Process-data model control sub-process
Plan
The Plan sub-process contains activities that in cooperation with the Service Level Management lead to the (information) Security section in the SLA. Furthermore, the Plan sub-process contains activities that are related to the underpinning contracts which are specific for (information) security.
In the Plan sub-process the goals formulated in the SLA are specified in the form of Operational Level Agreements (OLA). These OLA’s can be defined as security plans for a specific internal organization entity of the service provider.
Besides the input of the SLA, the Plan sub-process also works with the policy statements of the service provider itself. As said earlier these policy statements are defined in the control sub-process.
The Operational Level Agreements for information security are setup and implemented based on the ITIL process. This means that there has to be cooperation with other ITIL processes. For example if the security management wishes to change the IT infrastructure in order to achieve maximum security, these changes will only be done through the Change Management process. The Security Management will deliver the input (Request for change) for this change. The change Manager is responsible for the Change Management Process itself.
TABLE 2.3.1: Activity Plan the (Sub) Activities and their Definition.
| Activities | Sub-Activities | Descriptions |
| Plan | Create Security section for SLA | This process contains activities that lead to the security agreements paragraph in the service level agreements. At the end of this process the SECURITY SECTION OF THE SERVICE LEVEL AGREEMENTS is created. |
| Plan | Create underpinning Contracts | This process contains activities that lead to UNDERPINNING CONTRACTS. These contracts are specific for security. |
| Plan | Create Operational level agreements | The general formulated goals in the SLA are specified in OPERATIONAL LEVEL AGREEMENTS. The OPERATIONAL LEVEL AGREEMENTS can be seen as security plans for specific organization units. |
| Plan | Reporting | In this process the whole Create plan process is documented in a specific way. This process ends with REPORTS. |
As well as for the Control sub-process the Plan sub-process has been modeled using the meta-modeling technique. On the right side of figure 2.2.1 the meta-process model of the plan sub-process is given.
As you can see the plan sub-process consists of a combination of unordered and ordered (sub) activities. Furthermore, it is noticeable that the sub-process contains three complex activities which are all closed activities and one standard activity.
Table 2.2.1 consists of concepts that are created or adjusted during the plan sub-process. The table also gives a definition of these concepts.
TABLE 2.2.1: Sub Activities and Description Plan Sub-Process ITIL Security Management.
| Concept | Descriptions |
| Plan | Formulated schemes for the security agreements. |
| Security Section of the Security Level Agreement | The security agreements paragraph in the written agreements between a Service Provider and the customer(s) that documents agreed Service Levels for a service. |
| Underpinning Contracts | A contract with an external supplier covering delivery of services that support the IT organisation in their delivery of services. |
| Operational Level Agreements | An internal agreement covering the delivery of services which support the IT organization in their delivery of services. |
Table 2.2.2: Concept and definition Plan sub-process Security management.
Just as the Control sub-process the Plan sub-process is modeled using the meta-modeling technique. The left side of figure 2.2.1 is the meta-data model of the Plan sub-process.
The plan rectangle is an open (complex) concept which has an aggregation type of relationship with two closed (complex) concepts and one standard concept. The two closed concepts are not expanded in this particular context.
The following picture (figure 2.2.1) is the process-data diagram of the Plan sub-process. This picture shows the integration of the two models. The dotted arrows indicate which concepts are created or adjusted in the corresponding activities of the Plan sub-process.
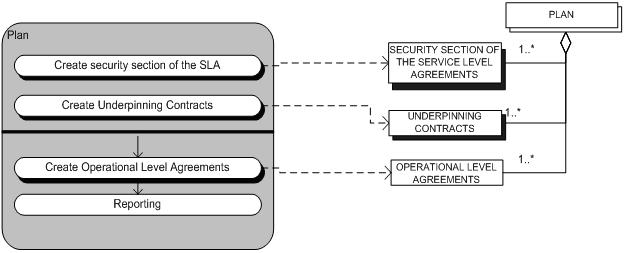
Figure 2.2.1: Process-data Model Plan sub-process
Implementation
The Implementation sub-process makes sure that all measures, as specified in the plans, are properly implemented. During the Implementation sub-process no (new) measures are defined nor changed. The definition or change of measures will take place in the Plan sub-process in cooperation with the Change Management Process.
The activities that take place in the implementation sub-process are summed up in the following table (table 2.3.1). The table contains the name of the (sub) activity and a short definition of the activity.
TABLE 2.3.1: Sub-Activities and Descriptions Implementation Sub-Process ITIL Security Management.
| Activities | Sub-Activities | Descriptions |
| Implement | Classify and managing of IT applications. | Process of formally grouping configuration items by type, e.g., software, hardware, documentation, environment, application. Process of formally identifying changes by type e.g., project scope change request, validation change request, infrastructure change request this process leads to Asset Classification and Control Documents. |
| Implement | Implement personnel Security | Here measures are adopted in order to give personnel safety and confidence and measures to prevent a crime and or fraud. The process ends with Personal Security. |
| Implement | Implement Secure Management | In this process specific security requirements and or security rules that must be met are outlined and documented. The process ends with Security Policies. |
| Implement | Implement Access control | In this process specific access security requirements and or access security rules that must be met are outlined and documented. The process ends with Access Control. |
| Implement | Reporting | In this process the whole Implement as planned process is documented in a specific way. This process ends with Reports. |
The left side of figure 2.3.1 is the meta-process model of the Implementation phase. The four labels with a black shadow mean that these activities are closed concepts and they are not expanded in this context. It is also noticeable that there are no arrows connecting these four activities this means that these activities are unordered and the reporting will be carried out after the completion of all four activities.
During the implementation phase there are a number of concepts that are created and or adjusted. See table 2.3.2 for an overview of the most common concepts and their description.
TABLE 2.3.2: Concept and Definition Implementation Sub-Process Security Management.
| Concept | Description |
| Implementation | Accomplished security management according to the SECURITY MANAGEMENT PLAN. |
| Asset Classification and Control Documents | A comprehensive inventory of assets with responsibility assigned to ensure that effective security protection is maintained. |
| Personnel Security | Well defined job descriptions for all staff outlining security roles and responsibilities. |
| Security Policies | Security Policies are documents that outlines specific security requirements or security rules that must be met. |
| Access Control | Network management to ensure that only those with the appropriate responsibility have access to information in the networks and the protection of the supporting infrastructure. |
The concepts created and or adjusted are modeled using the meta-modeling technique. The right side of figure 2.3.1 is the meta-data model of the implementation sub-process.
The Implementation Documents is an open concept and is expanded in this context. It consists of four closed concepts which are not expanded because they are irrelevant in this particular context.
In order to make the relations between the two models clearer the integration of the two models are illustrated in figure 2.3.1. The dotted arrows running from the activities to the concepts illustrate which concepts are created or adjusted in the corresponding activities.
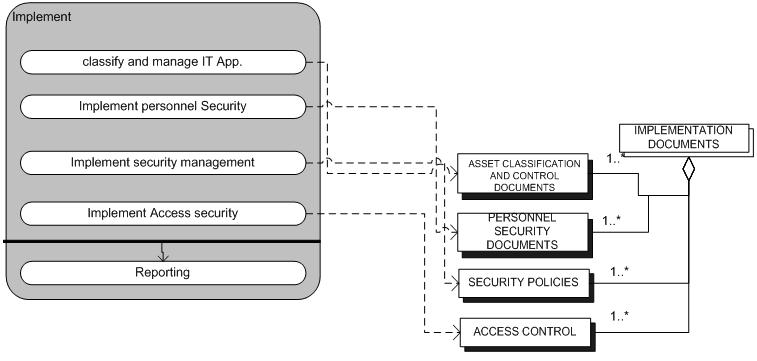
Figure 2.3.1: Process-data model Implementation sub-process
Evaluation
The evaluation of the implementation and the plans is very important. The evaluation is necessary to measure the success of the implementation and the Security plans. The evaluation is also very important for the clients (and possibly third parties). The results of the Evaluation sub-process are used to maintain the agreed measures and the implementation itself. Evaluation results can lead to new requirements and so lead to a request for change. The request for change is then defined and it is then send to the Change Management process.
Mainly there are three sorts of evaluation; the Self assessment; internal audit, and external audit.
The self assessment is mainly carried out in the organization of the processes. The internal audits are carried out by internal IT-auditors and the external audits are carried out by external independent IT-auditors. Besides, the evaluations already mentioned an evaluation based on the communicated security incidents will also take place. The most important activities for this evaluation are the security monitoring of IT-systems; verify if the security legislation and the implementation of the security plans are complied; trace and react to undesirable use of the IT-supplies.
The activities that take place in the evaluation sub-process are summed up in the following table (Table 2.4.1). The table contains the name of the (sub) activity and a short definition of the activity.
TABLE 2.4.1: Sub-Activities and Descriptions Evaluation Sub-Process ITIL Security Management.
| Activities | Sub-Activities | Description |
| Evaluate | Self Assessment. | In this process an examination of the implemented security agreements is done by the organization of the process it self. The result of this process is Self Assessment Documents. |
| Evaluate | Internal Audit. | In this process an examination of the implemented security agreements is done by an internal EDP auditor. The result of this process is Internal Audit. |
| Evaluate | External Audit. | In this process an examination of the implemented security agreements is done by an external EDP auditor. The result of this process is External Audit. |
| Evaluate | Evaluation based on security incidents. | In this process an examination of the implemented security agreements is done based on security events which is not part of the standard operation of a service and which causes, or may cause, an interruption to, or a reduction in, the quality of that service. The result of this process is SECURITY INCIDENTS. |
| Evaluate | Reporting. | In this process the whole Evaluate implementation process is documented in a specific way. This process ends with reports. |
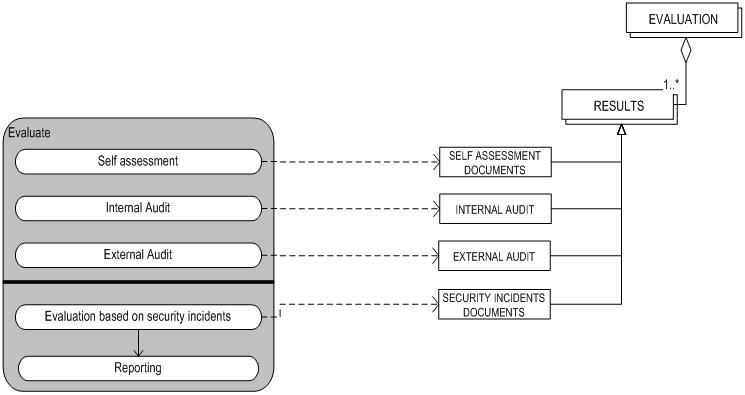
Figure 2.4.1: Process-data model Evaluation sub-process
The process-data diagram illustrated in the figure 2.4.1 consists of a meta-process model and a meta-data model. The Evaluation sub-process was modeled using the meta-modeling technique. The dotted arrows running from the meta-process diagram (left) to the meta-data diagram (right) indicate which concepts are created or adjusted in the corresponding activities. All of the activities in the evaluation phase are standard activities. For a short description of the Evaluation phase concepts see Table 2.4.2 where the concepts are listed and defined.
TABLE 2.4.2: Concept and Definition Evaluation Sub-Process Security Management.
| Description | Description |
| Evaluation | Evaluate or check implementation. |
| Results | The outcome of the evaluated implementation. |
| Self Assessment Documents | Result of the examination of the security management by the organization of the process it self. |
| Internal Audit | Result of the examination of the security management by the internal EDP auditor. |
| External Audit | Result of the examination of the security management by the external EDP auditor. |
| Security Incident Documents | Results of evaluating security events which is not part of the standard operation of a service and which causes, or may cause, an interruption to, or a reduction in, the quality of that service. |
Maintenance
It is necessary for the security to be maintained. Because of changes in the IT-infrastructure and changes in the organization itself security risks are bound to change over time. The maintenance of the security concerns both the maintenance of the security section of the service level agreements and the more detailed security plans.
The maintenance is based on the results of the Evaluation sub-process and insight in the changing risks. These activities will only produce proposals. The proposals serve as inputs for the plan sub-process and will go through the whole cycle or the proposals can be taken in the maintenance of the service level agreements. In both cases the proposals could lead to activities in the action plan. The actual changes will be carried by the Change Management process.
The activities that take place in the maintain sub-process are summed up in the following table (Table 2.5.1). The table contains the name of the (sub) activity and a short definition of the activity.
TABLE 2.5.1: Sub-Activities and descriptions Maintenance sub-process ITIL Security Management.
| Activities | Sub-Activities | Description |
| Maintain | Maintenance of service level agreements. | This is a process to keep the service level agreements in proper condition. The process ends with Maintained Service Level Agreements. |
| Maintain | Maintenance of operational level agreements. | This is a process to keep the operational level agreements in proper condition. The process ends with Maintained Operational Level Agreement. |
| Maintain | Request for change to SLA or OLA. | Request for a change to the SLA and or OLA is formulated. This process ends with a Request For Change. |
| Maintain | Reporting. | In this process the whole maintain implemented security policies process is documented in a specific way. This process ends with Reports. |
Figure 2.5.1 is the process-data diagram of the implementation sub-process. This picture shows the integration of the meta-process model (left) and the meta-data model (right). The dotted arrows indicate which concepts are created or adjusted in the activities of the implementation phase.
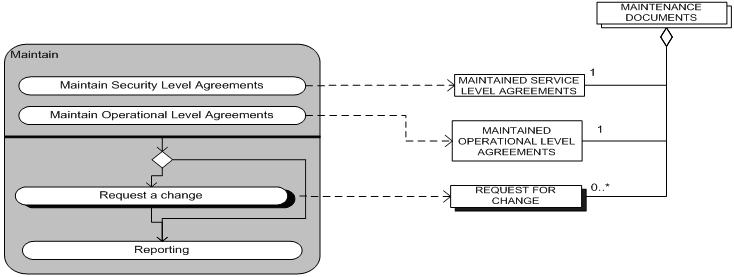
Figure 2.5.1: Process-data model Maintenance sub-process.
The maintenance sub-process starts with the maintenance of the service level agreements and the maintenance of the operational level agreements. After these activities take place (in no particular order) and there is a request for a change the request for change activity will take place and after the request for change activity is concluded the reporting activity starts. If there is no request for a change then the reporting activity will start directly after the first two activities. The concepts in the meta-data model are created or adjusted during the maintenance phase. For a list of the concepts and their definition take a look at table 2.5.2.
TABLE 2.5.2: Concept and Definition Plan Sub-Process Security Management.
| Concept | Description |
| Maintenance Documents | Agreements kept in proper condition. |
| Maintained Service Level Agreements | Service Level Agreements(security paragraph) kept in proper condition. |
| Maintained Operational Level Agreements | Operational Level Agreements kept in proper condition. |
| Request For Change | Form or electronic process used to record details of a request for a change to the SLA or the OLA. |
Complete process-data model
The following picture shows the complete process-data model of the Security Management process. This means that the complete meta-process model and the complete meta-data model and the integrations of the two models of the Security Management process are shown.
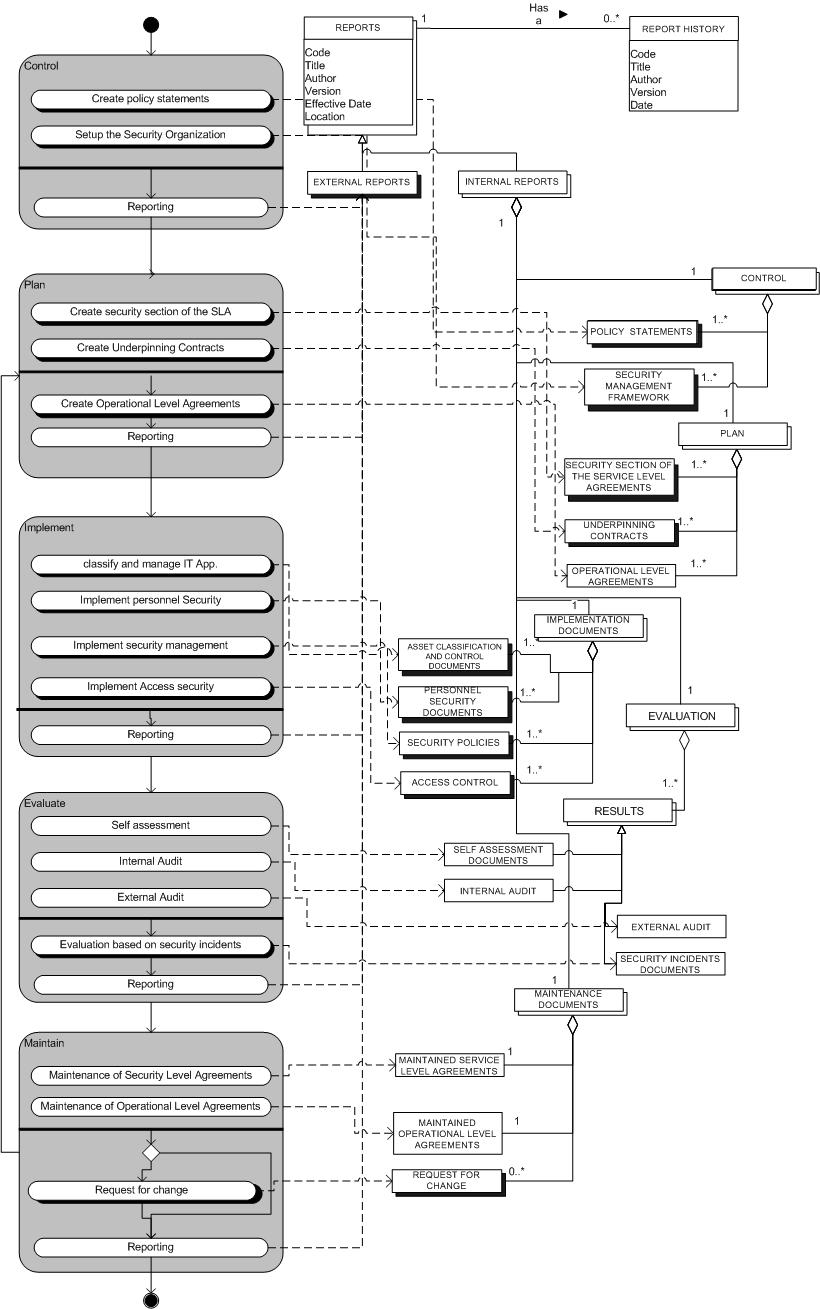
Figure 2.6.1: Process-Data Model Security Management Process.
Relations with other ITIL processes
The security Management Process, as stated in the introduction, has relations with almost al other ITIL-processes.
These processes are:
Within these processes there are a couple of activities concerning security that have to take place. These activities are done as required. The concerning process and its process manager are responsible for these activities. However, the Security Management will give indications to the concerning process on how these (security specific) activities should be structured.
Example
Email Policy.
The use of internal e-mail in an organization has a lot of security risks. So if an organization chooses to use e-mail as a means of communication, it is highly needed that the organization implements a well thought e-mail security plan/policies. In this example the ITIL security Management approach is used to implement e-mail policies in an organization.
First of the Security management team is formed and the guidelines, of how the process should be carried out, are formulated and made clear to all employees and provider concerned. These actions are carried out in the Control phase of the Security Management process.
The next step in to process to implement e-mail policies is the Planning. In the Plan phase of the process the policies are formulated. Besides the policies that are already written in the Service Level Agreements the policies that are specific for the e-mail security are formulated and added to the service level agreements. At the end of this phase the entire plan is formulated and is ready to be implemented.
The following phase in the process is the actual implementation of the e-mail policies. The implementation is done according to the plan which was formulated in the preceding phase (Plan phase).
After the actual implementation the e-mail policies will be evaluated. In order to evaluate the implemented policies the organization will perform;
The last phase is the maintenance phase. In the maintenance phase the implemented e-mail policies are maintained. The organization now knows which policies are properly implemented and are properly followed and, which policies need more work in order to help the security plan of the organization and, if there are new policies that have to be implemented. At the end of this process the Request for change are formulated (if needed) and the e-mail policies are properly maintained.
In order for the organization to keep its security plan up-to-date the organization will have to perform the security management process continuously. There is no end to this process an organization can always better its security.
The following picture gives an overview of the entire process of the Email Policy.
References
See: ISO 27001 Security Policy
Bon van, J. (2004). IT-Service management: een introductie op basis van ITIL. Van Haren Publishing
Cazemier, Jacques A.; Overbeek, Paul L.; Peters, Louk M. (2000). Security Management, Stationery Office.
Security management. (February 1, 2005). Retrieved from Microsoft Technet Web site: http://www.microsoft.com/technet/itsolutions/cits/mo/smf/mofsmsmf.mspx
Tse, D. (2005). Security in Modern Business: security assessment model for information security Practices. Hong Kong: University of Hong Kong.