Sample Configuration Management Standard:: Difference between revisions
No edit summary |
No edit summary |
||
| Line 1: | Line 1: | ||
== | ==Sample Configuration Management Standard== | ||
The Configuration Management Standard builds on the objectives established in the [[Sample_Asset_Management_Policy:|'''Asset Management Standard''']], and provides specific instructions and requirements for establishing and maintaining baseline protection standards for Company network devices, servers, and desktops. | |||
==Objectives== | |||
# '''General''' | |||
## Protection standards must be established and implemented for all computing and network resources in the Company production environment. | |||
## In accordance with the objectives established in the Asset Protection Standard, Company protection standards shall include specific security requirements in the following areas: | |||
### Access Control | |||
#### Remote Access | |||
#### Physical Access | |||
#### Encryption | |||
#### Integrity Protection | |||
#### Availability Protection | |||
#### Anti-Virus | |||
#### Information Handling | |||
#### Auditing | |||
## Sample Protection Standards must be reviewed by the Information Security Department to ensure vulnerabilities are not introduced into the Company production environment. | |||
# '''Network Devices''' | |||
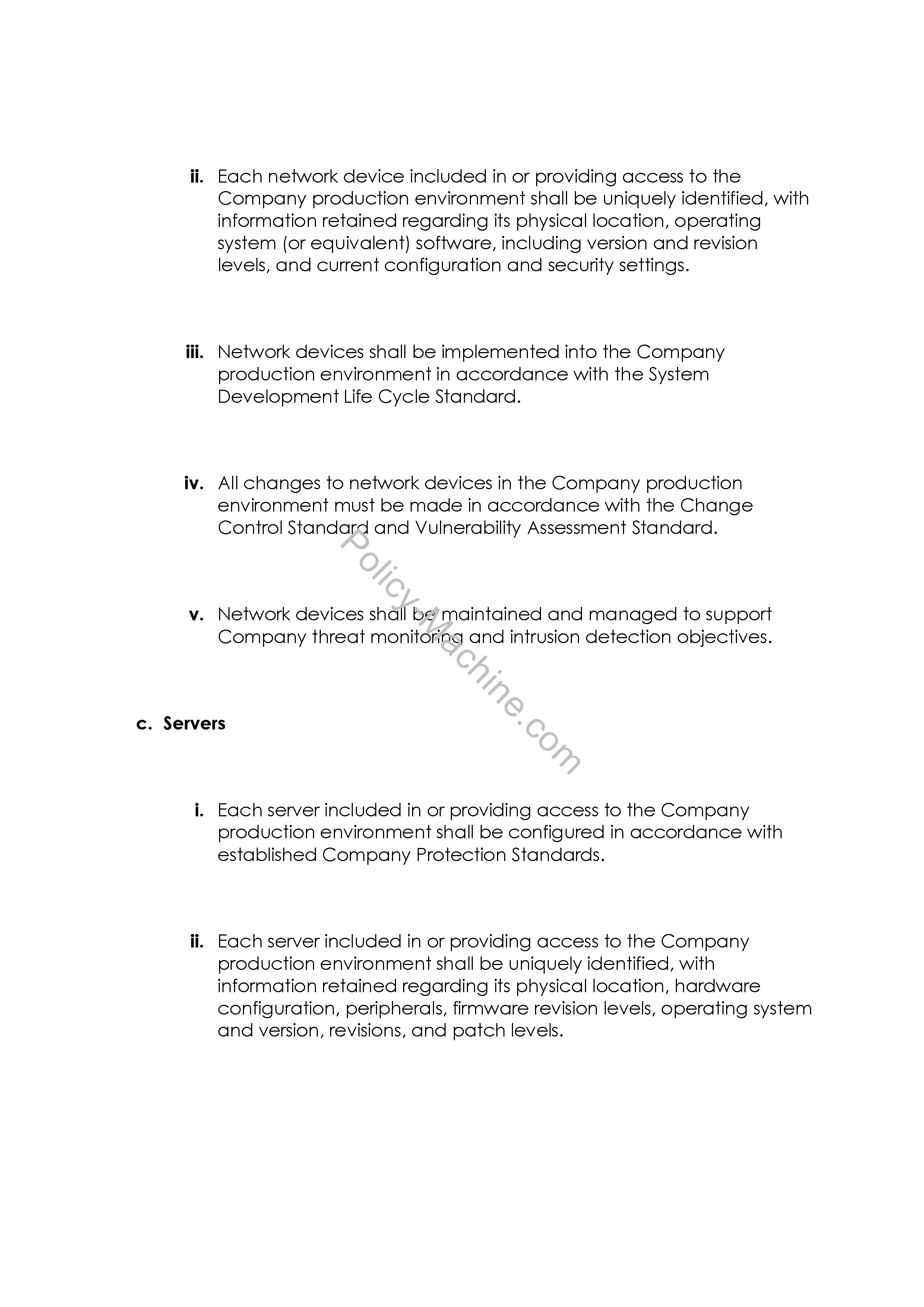
## Each network device included in or providing access to the Company production environment shall be configured in accordance with established Company protection standards. | |||
## Each network device included in or providing access to the Company production environment shall be uniquely identified, with information retained regarding its physical location, operating system (or equivalent) software, including version and revision levels, and current configuration and security settings. | |||
## Network devices shall be implemented into the Company production environment in accordance with the System Development Life Cycle Standard. | |||
## All changes to network devices in the Company production environment must be made in accordance with the Change Control Standard and Vulnerability Assessment Standard. | |||
## Network devices shall be maintained and managed to support Company threat monitoring and intrusion detection objectives. | |||
# '''Servers''' | |||
## Each server included in or providing access to the Company production environment shall be configured in accordance with established Company Protection Standards. | |||
## Each server included in or providing access to the Company production environment shall be uniquely identified, with information retained regarding its physical location, hardware configuration, peripherals, firmware revision levels, operating system and version, revisions, and patch levels. | |||
## Servers shall be implemented into the Company production environment in accordance with the [[Sample_System_Development_Life_Cycle_Standard:|'''System Development Life Cycle Standard''']]. | |||
## All changes to servers in the Company production environment must be made in accordance with the [[[Sample_Change_Control_Standard:|'''Change Control Certification Standard''']] and [[Sample_Vulnerability_Assessment_Standard:|'''Vulnerability Assessment Standard''']]. | |||
## Server configurations shall be checked for compliance to Company Protection Standards, at least monthly. | |||
## Servers shall be maintained and managed to support Company threat monitoring and intrusion detection objectives, and be in accordance with the [[Sample_Threat_Monitoring_Standard:|'''Threat Monitoring Standard''']] and [[Sample_Incident_Response_Standard:|'''Incident Response Standard''']]. | |||
# '''Desktop Environment''' | |||
## Standard desktop hardware and software configurations (that is, operating system, virus checking software, and common desktop tools or software) must be established, distributed, and maintained. | |||
## Unauthorized hardware or software shall not be installed on desktop or mobile computers. | |||
## Software packages, updates, and patches shall be distributed through approved predefined processes, and associated metrics shall be maintained, to determine success rates and compliance. | |||
## All changes to standard desktop hardware or software configurations must be made in accordance with the [[[Sample_Change_Control_Standard:|'''Change Control Certification Standard''']] and [[Sample_Vulnerability_Assessment_Standard:|'''Vulnerability Assessment Standard''']]. | |||
## Desktop and mobile systems are subject to regular or unannounced audits of hardware and software to identify and remove non-compliant components. | |||
<br> | <br> | ||
==Document Examples== | |||
Use these samples as a guide for your policy development. Fully customizable versions are available from [http://policy-machine.com The Policy Machine].<br> | |||
<br> | |||
<br> | <br> | ||
<gallery> | |||
Image:Configuration Management Standard.png|Configuration Management Standard page one of nine. | |||
Image:Configuration Management Standard(1).png|Configuration Management Standard page two of nine. | |||
Image:Configuration Management Standard(2).png|Configuration Management Standard page three of nine. | |||
Image:Configuration Management Standard(3).png|Configuration Management Standard page four of nine. | |||
Image:Configuration Management Standard(4).png|Configuration Management Standard page five of nine. | |||
Image:Configuration Management Standard(5).png|Configuration Management Standard page six of nine. | |||
Image:Configuration Management Standard(6).png|Configuration Management Standard page seven of nine. | |||
Image:Configuration Management Standard(7).png|Configuration Management Standard page eight of nine. | |||
Image:Configuration Management Standard(8).png|Configuration Management Standard page nine of nine. | |||
</gallery> | |||
[[file:Configuration Management Standard.png]] | |||
[[file:Configuration Management Standard(1).png]] | |||
[[file:Configuration Management Standard(2).png]] | |||
[[file:Configuration Management Standard(3).png]] | |||
[[file:Configuration Management Standard(4).png]] | |||
[[file:Configuration Management Standard(5).png]] | |||
[[file:Configuration Management Standard(6).png]] | |||
[[file:Configuration Management Standard(7).png]] | |||
[[file:Configuration Management Standard(8).png]] | |||
: | |||
Revision as of 21:17, 15 January 2014
Sample Configuration Management Standard
The Configuration Management Standard builds on the objectives established in the Asset Management Standard, and provides specific instructions and requirements for establishing and maintaining baseline protection standards for Company network devices, servers, and desktops.
Objectives
- General
- Protection standards must be established and implemented for all computing and network resources in the Company production environment.
- In accordance with the objectives established in the Asset Protection Standard, Company protection standards shall include specific security requirements in the following areas:
- Access Control
- Remote Access
- Physical Access
- Encryption
- Integrity Protection
- Availability Protection
- Anti-Virus
- Information Handling
- Auditing
- Access Control
- Sample Protection Standards must be reviewed by the Information Security Department to ensure vulnerabilities are not introduced into the Company production environment.
- Network Devices
- Each network device included in or providing access to the Company production environment shall be configured in accordance with established Company protection standards.
- Each network device included in or providing access to the Company production environment shall be uniquely identified, with information retained regarding its physical location, operating system (or equivalent) software, including version and revision levels, and current configuration and security settings.
- Network devices shall be implemented into the Company production environment in accordance with the System Development Life Cycle Standard.
- All changes to network devices in the Company production environment must be made in accordance with the Change Control Standard and Vulnerability Assessment Standard.
- Network devices shall be maintained and managed to support Company threat monitoring and intrusion detection objectives.
- Servers
- Each server included in or providing access to the Company production environment shall be configured in accordance with established Company Protection Standards.
- Each server included in or providing access to the Company production environment shall be uniquely identified, with information retained regarding its physical location, hardware configuration, peripherals, firmware revision levels, operating system and version, revisions, and patch levels.
- Servers shall be implemented into the Company production environment in accordance with the System Development Life Cycle Standard.
- All changes to servers in the Company production environment must be made in accordance with the [[[Sample_Change_Control_Standard:|Change Control Certification Standard]] and Vulnerability Assessment Standard.
- Server configurations shall be checked for compliance to Company Protection Standards, at least monthly.
- Servers shall be maintained and managed to support Company threat monitoring and intrusion detection objectives, and be in accordance with the Threat Monitoring Standard and Incident Response Standard.
- Desktop Environment
- Standard desktop hardware and software configurations (that is, operating system, virus checking software, and common desktop tools or software) must be established, distributed, and maintained.
- Unauthorized hardware or software shall not be installed on desktop or mobile computers.
- Software packages, updates, and patches shall be distributed through approved predefined processes, and associated metrics shall be maintained, to determine success rates and compliance.
- All changes to standard desktop hardware or software configurations must be made in accordance with the [[[Sample_Change_Control_Standard:|Change Control Certification Standard]] and Vulnerability Assessment Standard.
- Desktop and mobile systems are subject to regular or unannounced audits of hardware and software to identify and remove non-compliant components.
Document Examples
Use these samples as a guide for your policy development. Fully customizable versions are available from The Policy Machine.
-
Configuration Management Standard page one of nine.
-
Configuration Management Standard page two of nine.
-
Configuration Management Standard page three of nine.
-
Configuration Management Standard page four of nine.
-
Configuration Management Standard page five of nine.
-
Configuration Management Standard page six of nine.
-
Configuration Management Standard page seven of nine.
-
Configuration Management Standard page eight of nine.
-
Configuration Management Standard page nine of nine.