PCI 4:: Difference between revisions
Jump to navigation
Jump to search
No edit summary |
No edit summary |
||
| (3 intermediate revisions by the same user not shown) | |||
| Line 7: | Line 7: | ||
---- | ---- | ||
<br> | <br> | ||
:'''PCI-4.1 Use strong cryptography and encryption techniques (at least 128 bit) such as Secure Sockets Layer (SSL), Point-to-Point Tunneling Protocol (PPTP), Internet Protocol Security (IPSEC) to safeguard sensitive cardholder data during transmission over public networks.'''<br> | :'''PCI-4.1 Use strong cryptography and [[Encryption | encryption]] techniques (at least 128 bit) such as Secure Sockets Layer (SSL), Point-to-Point Tunneling Protocol (PPTP), Internet Protocol Security (IPSEC) to safeguard sensitive cardholder data during transmission over public networks.'''<br> | ||
<br> | <br> | ||
::'''Verify the use of encryption (e.g., SSL) wherever cardholder data is transmitted or received over the Internet by performing the following:'''<br> | ::'''Verify the use of [[Encryption | encryption]] (e.g., SSL) wherever cardholder data is transmitted or received over the Internet by performing the following:'''<br> | ||
<br> | <br> | ||
::* Verify that at least 128 bit encryption is used during data transmission. | ::* Verify that at least 128 bit [[Encryption | encryption]] is used during data transmission. | ||
::* For SSL implementations, verify that HTTPS appears as a part of the browser Universal Record Locator (URL), and that no cardholder data was required when HTTPS did not appear in the URL. | ::* For SSL implementations, verify that HTTPS appears as a part of the browser Universal Record Locator (URL), and that no cardholder data was required when HTTPS did not appear in the URL. | ||
::* Select a sample of transactions as they are received and observe transactions as they occur to verify that cardholder data is encrypted during transit. | ::* Select a sample of transactions as they are received and observe transactions as they occur to verify that cardholder data is encrypted during transit. | ||
::* Verify that only trusted SSL keys/certificates are accepted.<br> | ::* Verify that only trusted SSL keys/certificates are accepted.<br> | ||
<br> | <br> | ||
::'''Verify that, for the encryption methodology in use, the proper encryption strength is implemented. For example:'''<br> | ::'''Verify that, for the [[Encryption | encryption]] methodology in use, the proper [[Encryption | encryption]] strength is implemented. For example:'''<br> | ||
<br> | <br> | ||
::* 3DES: 128 bits | ::* 3DES: 128 bits | ||
::* AES: 256 bits | ::* [[AES | Advanced Encryption Standard]] (AES): 256 bits | ||
::* RSA: 1024 bits | ::* RSA: 1024 bits | ||
::* Check vendor recommendations and best practices for other encryption methodologies. | ::* Check vendor recommendations and best practices for other [[Encryption | encryption]] methodologies. | ||
<br> | <br> | ||
::[[Image:Key-control.jpg]][[PCI-4.1.1:|PCI-4.1.1 For wireless networks transmitting cardholder data, encrypt the transmissions by using Wi-Fi Protected Access (WPA) technology if WPA capable, or VPN or SSL at 128-bit. Never rely exclusively on WEP to protect confidentiality and access to a wireless LAN. Use one of the above methodologies in conjunction with WEP at 128 bit, and rotate shared WEP keys quarterly and whenever there are personnel changes.]]<br> | ::[[Image:Key-control.jpg]][[PCI-4.1.1:|PCI-4.1.1 For wireless networks transmitting cardholder data, encrypt the transmissions by using Wi-Fi Protected Access (WPA) technology if WPA capable, or VPN or SSL at 128-bit. Never rely exclusively on WEP to protect confidentiality and access to a wireless LAN. Use one of the above methodologies in conjunction with WEP at 128 bit, and rotate shared WEP keys quarterly and whenever there are personnel changes.]]<br> | ||
| Line 31: | Line 31: | ||
::*'''Maintain a Vulnerability Management Program.''' | ::*'''Maintain a Vulnerability Management Program.''' | ||
<br> | <br> | ||
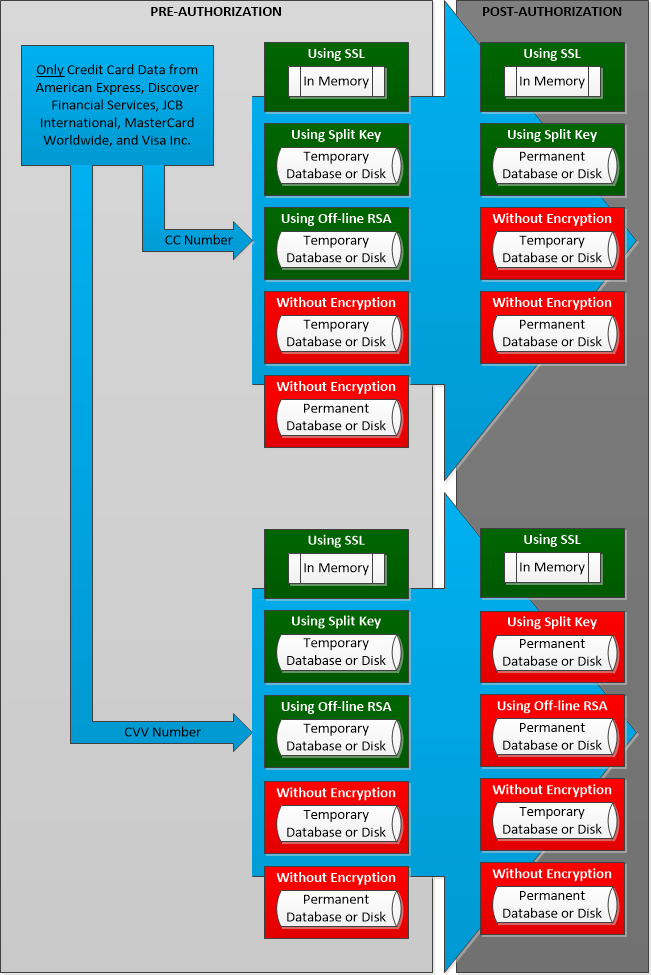
Use this illustration to determine what and where card data is permitted by PCI DSS.<br> | |||
<br> | |||
[[File:PCI-DSS-V3-CardFlow.png]] | |||
--[[User:Mdpeters|Mdpeters]] 08:33, 7 July 2006 (EDT) | --[[User:Mdpeters|Mdpeters]] 08:33, 7 July 2006 (EDT) | ||
Latest revision as of 12:22, 31 January 2014
Requirement 4: Encrypt transmission of cardholder data and sensitive information across public networks.
- Note that this does not apply to those employees and other parties with a specific need to see full credit card numbers.
- PCI-4.1 Use strong cryptography and encryption techniques (at least 128 bit) such as Secure Sockets Layer (SSL), Point-to-Point Tunneling Protocol (PPTP), Internet Protocol Security (IPSEC) to safeguard sensitive cardholder data during transmission over public networks.
- Verify the use of encryption (e.g., SSL) wherever cardholder data is transmitted or received over the Internet by performing the following:
- Verify the use of encryption (e.g., SSL) wherever cardholder data is transmitted or received over the Internet by performing the following:
- Verify that at least 128 bit encryption is used during data transmission.
- For SSL implementations, verify that HTTPS appears as a part of the browser Universal Record Locator (URL), and that no cardholder data was required when HTTPS did not appear in the URL.
- Select a sample of transactions as they are received and observe transactions as they occur to verify that cardholder data is encrypted during transit.
- Verify that only trusted SSL keys/certificates are accepted.
- Verify that, for the encryption methodology in use, the proper encryption strength is implemented. For example:
- Verify that, for the encryption methodology in use, the proper encryption strength is implemented. For example:
- 3DES: 128 bits
- Advanced Encryption Standard (AES): 256 bits
- RSA: 1024 bits
- Check vendor recommendations and best practices for other encryption methodologies.
 PCI-4.1.1 For wireless networks transmitting cardholder data, encrypt the transmissions by using Wi-Fi Protected Access (WPA) technology if WPA capable, or VPN or SSL at 128-bit. Never rely exclusively on WEP to protect confidentiality and access to a wireless LAN. Use one of the above methodologies in conjunction with WEP at 128 bit, and rotate shared WEP keys quarterly and whenever there are personnel changes.
PCI-4.1.1 For wireless networks transmitting cardholder data, encrypt the transmissions by using Wi-Fi Protected Access (WPA) technology if WPA capable, or VPN or SSL at 128-bit. Never rely exclusively on WEP to protect confidentiality and access to a wireless LAN. Use one of the above methodologies in conjunction with WEP at 128 bit, and rotate shared WEP keys quarterly and whenever there are personnel changes.
- Maintain a Vulnerability Management Program.
Use this illustration to determine what and where card data is permitted by PCI DSS.
--Mdpeters 08:33, 7 July 2006 (EDT)