PO4.11:: Difference between revisions
No edit summary |
No edit summary |
||
| (One intermediate revision by the same user not shown) | |||
| Line 1: | Line 1: | ||
==PO 4.11 Segregation of Duties== | |||
==Control Objective:== | |||
Implement a division of roles and responsibilities that reduces the possibility for a single individual to subvert a critical process. Management also makes sure that personnel are performing only authorized duties relevant to their respective jobs and positions.<br> | Implement a division of roles and responsibilities that reduces the possibility for a single individual to subvert a critical process. Management also makes sure that personnel are performing only authorized duties relevant to their respective jobs and positions.<br> | ||
<br> | <br> | ||
==Applicability:== | |||
:: '''Sarbanes-Oxley''' | :: '''Sarbanes-Oxley''' | ||
:: HIPAA | :: HIPAA | ||
| Line 17: | Line 14: | ||
:: User Defined | :: User Defined | ||
<br> | <br> | ||
==Risk Association Control Activities:== | |||
::'''1. Risk: Segregation of duties may be compromised and unauthorized activity may occur.'''<br> | ::'''1. Risk: Segregation of duties may be compromised and unauthorized activity may occur.'''<br> | ||
:::a. SOX.7.1.1: Access to particular functions within applications (e.g., approving payment of vendors) should be appropriately restricted to ensure segregation of duties and prevent unauthorized activity.<br> | :::a. SOX.7.1.1: Access to particular functions within applications (e.g., approving payment of vendors) should be appropriately restricted to ensure segregation of duties and prevent unauthorized activity.<br> | ||
<br> | <br> | ||
::'''2. Risk: Conflicting access credential may violate confidentiality, privacy, or possible data loss.'''<br> | ::'''2. Risk: Conflicting access credential may violate confidentiality, [[privacy]], or possible data loss.'''<br> | ||
:::a. SOX.2.0.4: Segregation of duties for staff, both within the IT Department and between IT and user functions is adequate to prevent the same individual from performing incompatible functions.<br> | :::a. SOX.2.0.4: Segregation of duties for staff, both within the IT Department and between IT and user functions is adequate to prevent the same individual from performing incompatible functions.<br> | ||
<br> | <br> | ||
==Implementation Guide:== | |||
==Process Narrative== | |||
All Data Center personnel are issued picture identification cards that must be worn at all times. These identification cards also serve as card keys for entrance into and exit out of the facility. The magnetic strip on the card key controls (via a computerized security system) an employee's access rights to various locations within the building, including the Data Center.<br> | All Data Center personnel are issued picture identification cards that must be worn at all times. These identification cards also serve as card keys for entrance into and exit out of the facility. The magnetic strip on the card key controls (via a computerized security system) an employee's access rights to various locations within the building, including the Data Center.<br> | ||
<br> | <br> | ||
==Process Illustration== | |||
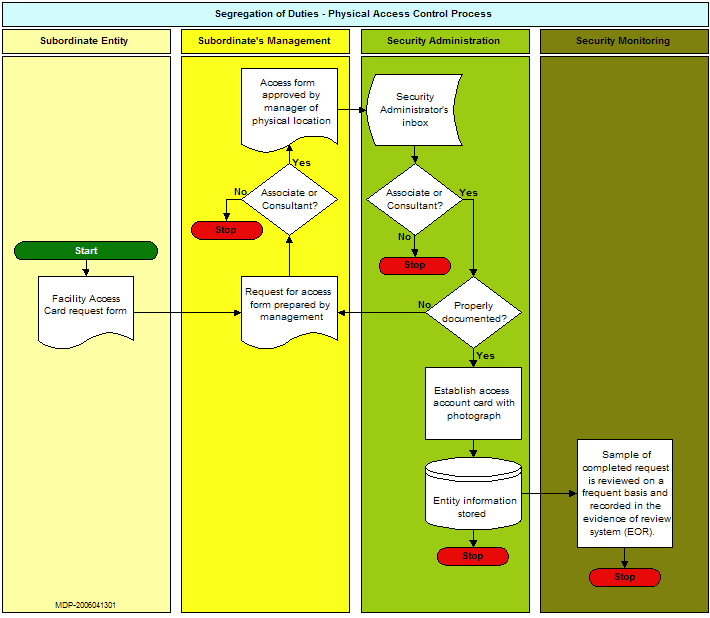
The following illustration represents an adequate level of segregation between the entity gaining access and the individual granting access. The diagram illustrates segregation of duties as it applies to physical security within the enterprise.<br> | The following illustration represents an adequate level of segregation between the entity gaining access and the individual granting access. The diagram illustrates segregation of duties as it applies to physical security within the enterprise.<br> | ||
<br> | <br> | ||
[[Image:physical-access-process.jpg]]<br> | [[Image:physical-access-process.jpg]]<br> | ||
<br> | <br> | ||
==Control Commentary== | |||
Preventing a single entity from possessing all the power to assume power and control is the objective behind segregation of duties. A single manager or responsible representative may most certainly make an access request at any time. A controlled and fully documented process should exist either in simple paper format or a more elaborate electronic mechanism is required. Having the ability to identify with certainty the chain of events traversing the request and approval process is paramount. Another vital component comes from independent monitoring of access changes that occur with the enterprise.<br> | Preventing a single entity from possessing all the power to assume power and control is the objective behind segregation of duties. A single manager or responsible representative may most certainly make an access request at any time. A controlled and fully documented process should exist either in simple paper format or a more elaborate electronic mechanism is required. Having the ability to identify with certainty the chain of events traversing the request and approval process is paramount. Another vital component comes from independent monitoring of access changes that occur with the enterprise.<br> | ||
<br> | <br> | ||
==Control Exception Commentary== | |||
Insert a description of the control exception that is applicable to the existing control statement this commentary refers to.<br> | Insert a description of the control exception that is applicable to the existing control statement this commentary refers to.<br> | ||
<br> | <br> | ||
==Evidence Archive Location== | |||
Insert Evidence Description Here.<br> | Insert Evidence Description Here.<br> | ||
<br> | <br> | ||
==Control Status and Auditors Commentary== | |||
Describe the condition of the applicable control and its effectiveness. Set the color icon to a redlock.jpg, yellowlock.jpg or greenlock.jpg.<br> | Describe the condition of the applicable control and its effectiveness. Set the color icon to a redlock.jpg, yellowlock.jpg or greenlock.jpg.<br> | ||
<br> | <br> | ||
[[Image:yellowlock.jpg]]<br> | [[Image:yellowlock.jpg]]<br> | ||
<br> | <br> | ||
==Remediation Plan== | |||
Insert remediation plan, applicability, or any information that indicates what needs to be done.<br> | Insert remediation plan, applicability, or any information that indicates what needs to be done.<br> | ||
<br> | <br> | ||
==Supplemental Information:== | |||
ISO | ISO 27002 10.1.3 Duties and areas of responsibility should be segregated to reduce opportunities for unauthorized or unintentional modification or misuse of the organization’s assets.<br> | ||
<br> | <br> | ||
==Implementation Guidance== | |||
Segregation of duties is a method for reducing the risk of accidental or deliberate system misuse. Care should be taken that no single person can access, modify or use assets without authorization or detection. The initiation of an event should be separated from its authorization. The possibility of collusion should be considered in designing the controls.<br> | Segregation of duties is a method for reducing the risk of accidental or deliberate system misuse. Care should be taken that no single person can access, modify or use assets without authorization or detection. The initiation of an event should be separated from its authorization. The possibility of collusion should be considered in designing the controls.<br> | ||
<br> | <br> | ||
Small organizations may find segregation of duties difficult to achieve, but the principle should be applied as far as is possible and practicable. Whenever it is difficult to segregate, other controls such as monitoring of activities, audit trails and management supervision should be considered. It is important that [[Information_Security_Audit | security audit]] remains independent.<br> | Small organizations may find segregation of duties difficult to achieve, but the principle should be applied as far as is possible and practicable. Whenever it is difficult to segregate, other controls such as monitoring of activities, audit trails and management supervision should be considered. It is important that [[Information_Security_Audit | security audit]] remains independent.<br> | ||
<br> | <br> | ||
Latest revision as of 19:45, 14 June 2007
PO 4.11 Segregation of Duties
Control Objective:
Implement a division of roles and responsibilities that reduces the possibility for a single individual to subvert a critical process. Management also makes sure that personnel are performing only authorized duties relevant to their respective jobs and positions.
Applicability:
- Sarbanes-Oxley
- HIPAA
- GLBA
- PCI
- FISMA
- NIST SP 800-66
- Ditscap
- Control Exception
- User Defined
Risk Association Control Activities:
- 1. Risk: Segregation of duties may be compromised and unauthorized activity may occur.
- a. SOX.7.1.1: Access to particular functions within applications (e.g., approving payment of vendors) should be appropriately restricted to ensure segregation of duties and prevent unauthorized activity.
- a. SOX.7.1.1: Access to particular functions within applications (e.g., approving payment of vendors) should be appropriately restricted to ensure segregation of duties and prevent unauthorized activity.
- 1. Risk: Segregation of duties may be compromised and unauthorized activity may occur.
- 2. Risk: Conflicting access credential may violate confidentiality, privacy, or possible data loss.
- a. SOX.2.0.4: Segregation of duties for staff, both within the IT Department and between IT and user functions is adequate to prevent the same individual from performing incompatible functions.
- a. SOX.2.0.4: Segregation of duties for staff, both within the IT Department and between IT and user functions is adequate to prevent the same individual from performing incompatible functions.
- 2. Risk: Conflicting access credential may violate confidentiality, privacy, or possible data loss.
Implementation Guide:
Process Narrative
All Data Center personnel are issued picture identification cards that must be worn at all times. These identification cards also serve as card keys for entrance into and exit out of the facility. The magnetic strip on the card key controls (via a computerized security system) an employee's access rights to various locations within the building, including the Data Center.
Process Illustration
The following illustration represents an adequate level of segregation between the entity gaining access and the individual granting access. The diagram illustrates segregation of duties as it applies to physical security within the enterprise.
Control Commentary
Preventing a single entity from possessing all the power to assume power and control is the objective behind segregation of duties. A single manager or responsible representative may most certainly make an access request at any time. A controlled and fully documented process should exist either in simple paper format or a more elaborate electronic mechanism is required. Having the ability to identify with certainty the chain of events traversing the request and approval process is paramount. Another vital component comes from independent monitoring of access changes that occur with the enterprise.
Control Exception Commentary
Insert a description of the control exception that is applicable to the existing control statement this commentary refers to.
Evidence Archive Location
Insert Evidence Description Here.
Control Status and Auditors Commentary
Describe the condition of the applicable control and its effectiveness. Set the color icon to a redlock.jpg, yellowlock.jpg or greenlock.jpg.
File:Yellowlock.jpg
Remediation Plan
Insert remediation plan, applicability, or any information that indicates what needs to be done.
Supplemental Information:
ISO 27002 10.1.3 Duties and areas of responsibility should be segregated to reduce opportunities for unauthorized or unintentional modification or misuse of the organization’s assets.
Implementation Guidance
Segregation of duties is a method for reducing the risk of accidental or deliberate system misuse. Care should be taken that no single person can access, modify or use assets without authorization or detection. The initiation of an event should be separated from its authorization. The possibility of collusion should be considered in designing the controls.
Small organizations may find segregation of duties difficult to achieve, but the principle should be applied as far as is possible and practicable. Whenever it is difficult to segregate, other controls such as monitoring of activities, audit trails and management supervision should be considered. It is important that security audit remains independent.