DS12.3:: Difference between revisions
No edit summary |
No edit summary |
||
| (3 intermediate revisions by the same user not shown) | |||
| Line 16: | Line 16: | ||
<br> | <br> | ||
'''Risk Association Control Activities:'''<br> | '''Risk Association Control Activities:'''<br> | ||
::''' | ::1. '''Risk: Third party service providers may not meet business, compliance and regulatory needs of the business inducing risk.'''<br> | ||
:::a. SOX.1.5: | :::a. [[SOX.1.5:|'''SOX.1.5''']] A designated individual is responsible for regular monitoring and reporting on the achievement of the third-party service-level performance criteria.<br> | ||
<br> | <br> | ||
::'''2. Risk: Computer equipment may be compromised by accidental damage.''' | ::'''2. Risk: Computer equipment may be compromised by accidental damage.''' | ||
:::a. SOX.2.6.1: Physical storage of computer equipment should be appropriately protected to prevent the risk of accidental damage (e.g., fire, flood, smoke, water, dust, vibration, chemicals, and radiation). | :::a. [[SOX.2.6.1:|'''SOX.2.6.1''']] Physical storage of computer equipment should be appropriately protected to prevent the risk of accidental damage (e.g., fire, flood, smoke, water, dust, vibration, chemicals, and radiation). | ||
<br> | <br> | ||
::'''3. Risk: Third party processors create unacceptable control risks to the Company. ''' | ::'''3. Risk: Third party processors create unacceptable control risks to the Company. ''' | ||
:::a. SOX.2.0.5: Selection of Vendors for outsourced services is performed in accordance with the organization's vendor management policy. | :::a. [[SOX.2.0.5:|'''SOX.2.0.5''']] Selection of Vendors for outsourced services is performed in accordance with the organization's vendor management policy. | ||
<br> | <br> | ||
* PCI-9.1.1 Use cameras to monitor sensitive areas. Audit this data and correlate with other entries. Store for at least three months, unless otherwise restricted by law. | |||
<br> | <br> | ||
* PCI-9.1.2 Restrict physical access to publicly accessible network jacks. | |||
<br> | <br> | ||
* PCI-9.1.3 Restrict physical access to wireless access points, gateways, and handheld devices. | |||
<br> | <br> | ||
* PCI.9.2: Develop procedures to help all personnel easily distinguish between employees and visitors, especially in areas where cardholder information is accessible. | |||
<br> | <br> | ||
* PCI-9.3.1 Authorized before entering areas where cardholder data is processed or maintained. | |||
<br> | <br> | ||
* PCI-9.3.2 Given a physical token (e.g., badge or access device) that expires, and that identifies them as non-employees. | |||
<br> | <br> | ||
* PCI-9.3.3 Asked to surrender the physical token before leaving the facility or at the date of expiration.PCI.9.4: Use a visitor log to retain a physical audit trail of visitor activity. Retain this log for a minimum of three months, unless otherwise restricted by law. | |||
:<br> | :<br> | ||
* PCI.9.6: Physically secure all paper and electronic media (e.g., computers, electronic media, networking and communications hardware, telecommunication lines, paper receipts, paper reports, and faxes) that contain cardholder information. | |||
<br> | <br> | ||
* PCI-9.7.1 Label the media so it can be identified as confidential. | |||
<br> | |||
* PCI-9.7.2 Send the media via secured courier or a delivery mechanism that can be accurately tracked. | |||
<br> | <br> | ||
'''Process Narrative'''<br> | '''Process Narrative'''<br> | ||
| Line 49: | Line 49: | ||
<br> | <br> | ||
'''Process Illustration'''<br> | '''Process Illustration'''<br> | ||
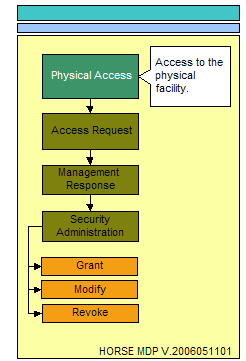
The following illustration represents the process flow for administering access to a physical resource. Examples of this would include the corporate data center. The physical location that surrounds critical data stores and the physical locations where electronic or local console access mechanisms exist providing a conduit to these critical data stores.<br> | |||
<br> | <br> | ||
[[Image: | [[Image:pysical-access-a.jpg]]<br> | ||
<br> | <br> | ||
'''Control Commentary'''<br> | '''Control Commentary'''<br> | ||
Latest revision as of 18:14, 21 June 2006
DS 12.3 Physical Access
Control Objective:
Define and implement procedures to grant, limit and revoke access to premises, buildings and areas according to business needs, including emergencies. Access to premises, buildings and areas should be justified, authorized, logged and monitored. This applies to all persons entering the premises, including staff, temporary staff, clients, vendors, visitors or any other third party.
Applicability:
- Sarbanes-Oxley
- HIPAA
- GLBA
- PCI
- FISMA
- NIST SP 800-66
- Ditscap
- Control Exception
- User Defined
Risk Association Control Activities:
- 1. Risk: Third party service providers may not meet business, compliance and regulatory needs of the business inducing risk.
- a. SOX.1.5 A designated individual is responsible for regular monitoring and reporting on the achievement of the third-party service-level performance criteria.
- a. SOX.1.5 A designated individual is responsible for regular monitoring and reporting on the achievement of the third-party service-level performance criteria.
- 1. Risk: Third party service providers may not meet business, compliance and regulatory needs of the business inducing risk.
- 2. Risk: Computer equipment may be compromised by accidental damage.
- a. SOX.2.6.1 Physical storage of computer equipment should be appropriately protected to prevent the risk of accidental damage (e.g., fire, flood, smoke, water, dust, vibration, chemicals, and radiation).
- 2. Risk: Computer equipment may be compromised by accidental damage.
- 3. Risk: Third party processors create unacceptable control risks to the Company.
- a. SOX.2.0.5 Selection of Vendors for outsourced services is performed in accordance with the organization's vendor management policy.
- 3. Risk: Third party processors create unacceptable control risks to the Company.
- PCI-9.1.1 Use cameras to monitor sensitive areas. Audit this data and correlate with other entries. Store for at least three months, unless otherwise restricted by law.
- PCI-9.1.2 Restrict physical access to publicly accessible network jacks.
- PCI-9.1.3 Restrict physical access to wireless access points, gateways, and handheld devices.
- PCI.9.2: Develop procedures to help all personnel easily distinguish between employees and visitors, especially in areas where cardholder information is accessible.
- PCI-9.3.1 Authorized before entering areas where cardholder data is processed or maintained.
- PCI-9.3.2 Given a physical token (e.g., badge or access device) that expires, and that identifies them as non-employees.
- PCI-9.3.3 Asked to surrender the physical token before leaving the facility or at the date of expiration.PCI.9.4: Use a visitor log to retain a physical audit trail of visitor activity. Retain this log for a minimum of three months, unless otherwise restricted by law.
- PCI.9.6: Physically secure all paper and electronic media (e.g., computers, electronic media, networking and communications hardware, telecommunication lines, paper receipts, paper reports, and faxes) that contain cardholder information.
- PCI-9.7.1 Label the media so it can be identified as confidential.
- PCI-9.7.2 Send the media via secured courier or a delivery mechanism that can be accurately tracked.
Process Narrative
Insert a description of the process narration that is applicable to the existing control statement this narrative refers to.
Process Illustration
The following illustration represents the process flow for administering access to a physical resource. Examples of this would include the corporate data center. The physical location that surrounds critical data stores and the physical locations where electronic or local console access mechanisms exist providing a conduit to these critical data stores.
Control Commentary
Insert a description of the control that is applicable to the existing control statement this commentary refers to.
Control Exception Commentary
Insert a description of the control exception that is applicable to the existing control statement this commentary refers to.
Evidence Archive Location
Insert Evidence Description Here.
Control Status and Auditors Commentary
Describe the condition of the applicable control and its effectiveness. Set the color icon to a redlock.jpg, yellowlock.jpg or greenlock.jpg.
File:Redlock.jpg
Remediation Plan
Insert remediation plan, applicability, or any information that indicates what needs to be done.
Supplemental Information:
ISO 7.1 Secure areas
ISO 7.2 Equipment security
ISO 7.3 General controls
ISO 8.5 Network management
ISO 8.6 Media handling and security
ISO 4.1 Information security infrastructure
ISO 4.2 Security of third-party access
ISO 6.1 Security in job definition and resourcing
ISO 8.1 Operational procedures and responsibilities
ISO 9.3 User responsibilities