PO4.10:: Difference between revisions
No edit summary |
No edit summary |
||
| (3 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
'''PO 4.10 Supervision'''<br> | '''PO 4.10 Supervision'''<br> | ||
<br> | <br> | ||
'''Control Objective:''' | '''Control Objective:''' | ||
<br> | <br> | ||
Implement adequate supervisory practices in the IT function to ensure that roles and responsibilities are properly exercised, to assess whether all personnel have sufficient authority and resources to execute their roles and responsibilities, and to generally review key performance indicators.<br> | <br> | ||
Implement adequate supervisory practices in the IT function to ensure that roles and responsibilities are properly exercised, to assess whether all personnel have sufficient authority and resources to execute their roles and responsibilities, and to generally review key performance indicators. | |||
<br> | |||
<br> | |||
'''Rationale —''' The process of defining and managing service levels addresses how an organization meets the functional and operational expectations of its users and, ultimately, the objectives of the business. Roles and responsibilities are defined and an accountability and measurement model is used to determine if services are delivered as required. Deficiencies in this area could significantly impact financial reporting and disclosure of an entity. For instance, if systems are poorly managed or system functionality is not delivered as required, financial information may not be processed as intended. | |||
<br> | |||
<br> | <br> | ||
'''Applicability:'''<br> | '''Applicability:'''<br> | ||
| Line 17: | Line 22: | ||
:: User Defined | :: User Defined | ||
<br> | <br> | ||
'''Risk Association Control Activities:'''<br> | '''Risk Association Control Activities:''' | ||
<br> | |||
<br> | <br> | ||
::'''1. Risk: Users may have inappropriate access to the application system.'''<br> | ::'''1. Risk: Users may have inappropriate access to the application system.'''<br> | ||
:::a. SOX.5.1.1: Access to the application system is appropriately restricted to prevent unauthorized activity.<br> | :::a. SOX.5.1.1: Access to the application system is appropriately restricted to prevent unauthorized activity. | ||
<br> | |||
<br> | |||
::'''2. Risk: Poorly serviced systems do not deliver as required and financial information may not be processed as intended.'''<br> | |||
:::a. [[SOX.5.1.13:|'''SOX.5.1.13''']] A framework is defined to establish key performance indicators to manage service-level agreements, both internally and externally. | |||
<br> | |||
<br> | |||
'''Implementation Guide:''' | |||
<br> | <br> | ||
<br> | <br> | ||
'''Process Narrative'''<br> | '''Process Narrative'''<br> | ||
| Line 28: | Line 40: | ||
<br> | <br> | ||
'''Process Illustration'''<br> | '''Process Illustration'''<br> | ||
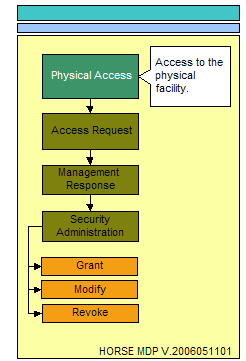
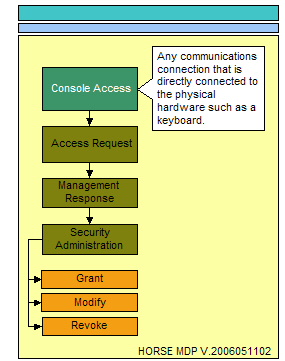
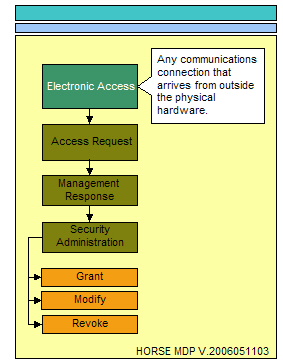
The following three illustrations represent the process flow for administering access to resources. The essence of access can only come in the form of physical access, electronic access, and local console access. The physical location that surrounds critical data stores and the physical locations where electronic or local console access mechanisms exist providing a conduit to critical data stores must be considered.<br> | |||
Physical access can be best described as the physical location that surrounds critical data stores and the physical locations where electronic or local console access mechanisms exist providing a conduit to these critical data stores.<br> | |||
<br> | |||
[[Image:pysical-access-a.jpg]]<br> | |||
<br> | |||
Console access can be best described as the location that has physical devices such as keyboards or USB ports providing a locally connected mechanism to access the system hosting critical data stores.<br> | |||
<br> | |||
[[Image:console-access-a.jpg]]<br> | |||
<br> | |||
Electronic access is best described as the various mechanisms used to access critical data stores and systems electronically. An example of this would be the Ethernet system connection, serial port or wireless access port that may be used to access the system hosting critical data stores. This connection is the most difficult to control due to the fact that there are so many ports, protocols, applications, and methodologies available to connect to systems electronically from anywhere in the world.<br> | |||
<br> | <br> | ||
[[Image: | [[Image:electronic-access-a.jpg]]<br> | ||
<br> | <br> | ||
'''Control Commentary'''<br> | '''Control Commentary'''<br> | ||
Insert a description of the control that is applicable to the existing control statement this commentary refers to.<br> | Insert a description of the control that is applicable to the existing control statement this commentary refers to.<br> | ||
Latest revision as of 15:23, 25 June 2006
PO 4.10 Supervision
Control Objective:
Implement adequate supervisory practices in the IT function to ensure that roles and responsibilities are properly exercised, to assess whether all personnel have sufficient authority and resources to execute their roles and responsibilities, and to generally review key performance indicators.
Rationale — The process of defining and managing service levels addresses how an organization meets the functional and operational expectations of its users and, ultimately, the objectives of the business. Roles and responsibilities are defined and an accountability and measurement model is used to determine if services are delivered as required. Deficiencies in this area could significantly impact financial reporting and disclosure of an entity. For instance, if systems are poorly managed or system functionality is not delivered as required, financial information may not be processed as intended.
Applicability:
- Sarbanes-Oxley
- HIPAA
- GLBA
- PCI
- FISMA
- NIST SP 800-66
- Ditscap
- Control Exception
- User Defined
Risk Association Control Activities:
- 1. Risk: Users may have inappropriate access to the application system.
- a. SOX.5.1.1: Access to the application system is appropriately restricted to prevent unauthorized activity.
- 1. Risk: Users may have inappropriate access to the application system.
- 2. Risk: Poorly serviced systems do not deliver as required and financial information may not be processed as intended.
- a. SOX.5.1.13 A framework is defined to establish key performance indicators to manage service-level agreements, both internally and externally.
- 2. Risk: Poorly serviced systems do not deliver as required and financial information may not be processed as intended.
Implementation Guide:
Process Narrative
Insert a description of the process narration that is applicable to the existing control statement this narrative refers to.
Process Illustration
The following three illustrations represent the process flow for administering access to resources. The essence of access can only come in the form of physical access, electronic access, and local console access. The physical location that surrounds critical data stores and the physical locations where electronic or local console access mechanisms exist providing a conduit to critical data stores must be considered.
Physical access can be best described as the physical location that surrounds critical data stores and the physical locations where electronic or local console access mechanisms exist providing a conduit to these critical data stores.
Console access can be best described as the location that has physical devices such as keyboards or USB ports providing a locally connected mechanism to access the system hosting critical data stores.
Electronic access is best described as the various mechanisms used to access critical data stores and systems electronically. An example of this would be the Ethernet system connection, serial port or wireless access port that may be used to access the system hosting critical data stores. This connection is the most difficult to control due to the fact that there are so many ports, protocols, applications, and methodologies available to connect to systems electronically from anywhere in the world.
Control Commentary
Insert a description of the control that is applicable to the existing control statement this commentary refers to.
Control Exception Commentary
Insert a description of the control exception that is applicable to the existing control statement this commentary refers to.
Evidence Archive Location
Insert Evidence Description Here.
Control Status and Auditors Commentary
Describe the condition of the applicable control and its effectiveness. Set the color icon to a redlock.jpg, yellowlock.jpg or greenlock.jpg.
File:Redlock.jpg
Remediation Plan
Insert remediation plan, applicability, or any information that indicates what needs to be done.
Supplemental Information:
ISO 17799 8.1 Operational procedures and responsibilities.
ISO 17799 8.5 Network management.
ISO 17799 9.7 Monitoring system access and use.
Implementation guidance
Insert guidance in this section if it helps to elaborate upon the subject matter. Examples of evidence that would help guide the end user is desirable.