DS5.4:
DS 5.4 User Account Management
Control Objective:
Ensure that requesting, establishing, issuing, suspending, modifying and closing user accounts and related user privileges are addressed by user account management. An approval procedure outlining the data or system owner granting the access privileges should be included. These procedures should apply for all users, including administrators (privileged users), internal and external users, for normal and emergency cases. Rights and obligations relative to access to enterprise systems and information are contractually arranged for all types of users. Perform regular management review of all accounts and related privileges.
Applicability:
- Sarbanes-Oxley
- HIPAA
- GLBA
- PCI
- FISMA
- NIST SP 800-66
- Ditscap
- Control Exception
- User Defined
Risk Association Control Activities:
- 1. Risk: Third party processors create unacceptable control risks to the Company.
- a. SOX.2.0.5: Selection of Vendors for outsourced services is performed in accordance with the organization's vendor management policy.
- a. SOX.2.0.5: Selection of Vendors for outsourced services is performed in accordance with the organization's vendor management policy.
- 1. Risk: Third party processors create unacceptable control risks to the Company.
- 2. Risk: Increased vulnerability may be exploited adversely impacting system availability, confidentiality and integrity of programs, processing and data.
- a. SOX.4.0.1: User accounts are set up individually for each employee and passwords are changed every XXX days. Default account passwords are changed.
- a. SOX.4.0.1: User accounts are set up individually for each employee and passwords are changed every XXX days. Default account passwords are changed.
- 2. Risk: Increased vulnerability may be exploited adversely impacting system availability, confidentiality and integrity of programs, processing and data.
- 3. Risk: Users may have inappropriate access to the application system.
- a. SOX.5.1.1: Access to the application system is appropriately restricted to prevent unauthorized activity.
- a. SOX.5.1.1: Access to the application system is appropriately restricted to prevent unauthorized activity.
- 3. Risk: Users may have inappropriate access to the application system.
- PCI.7.1: Limit access to computing resources and cardholder information to only those individuals whose job requires such access.
- PCI.7.2: Establish a mechanism for systems with multiple users that restricts access based on a user’s need to know, and is set to “deny all” unless specifically allowed.
- PCI-8.5.1 Control the addition, deletion, and modification of user IDs, credentials, and other identifier objects.
- PCI-8.5.2 Verify user identity before performing password resets.
- PCI-8.5.3 Set first-time passwords to a unique value per user and change immediately after first use.
- PCI-8.5.4 Immediately revokes accesses of terminated users.
- PCI-8.5.5 Remove inactive user accounts at least every 90 days.
- PCI-8.5.6 Enable accounts used by vendors for remote maintenance only during the time needed.
- PCI-8.5.7 Distribute password procedures and policies to all users who have access to cardholder information.
- PCI-8.5.8 Do not use group, shared, or generic accounts/passwords.
- PCI-8.5.9 Change user passwords at least every 90 days.
- PCI-8.5.10 Require a minimum password length of at least seven characters.
- PCI-8.5.11 Use passwords containing both numeric and alphabetic characters.
- PCI-8.5.12 Do not allow an individual to submit a new password that is the same as any of the last four passwords he or she has used.
- PCI-8.5.13 Limit repeated access attempts by locking out the user ID after not more than six attempts.
- PCI-8.5.14 the lockout duration to thirty minutes or until administrator enables the user ID.
- PCI-8.5.15 If a session has been idle for more than 15 minutes, require the user to reenter the password to reactivate the terminal.
- PCI-8.5.16 Authenticate all access to any database containing cardholder information. This includes access by applications, administrators, and all other users.
- PCI-12.5.1 Establish, document, and distribute security policies and procedures.
- PCI-12.5.2 Monitor and analyze security alerts and information, and distribute to appropriate personnel.
- PCI-12.5.3 Establish, document, and distribute security incident response and escalation procedures to ensure timely and effective handling of all situations.
- PCI-12.5.4 Administer user accounts, including additions, deletions, and modifications.
- PCI-12.5.5 Monitor and control all access to data.
Implementation Guide:
Process Narrative
The following illustration demonstrates how to test the effectiveness of account management processes for system accounts, application accounts, or physical security accounts. Known service and user accounts should be documented and these accounts should have management’s approval documented.
NOTE: A regular documented review process is required. A quarterly review and certification process in place will provide an adequate level of assurance for an annual compliance review.
Process Illustration
Insert a process diagram, flowchart or other visual representation here to illustrate the process narrative.
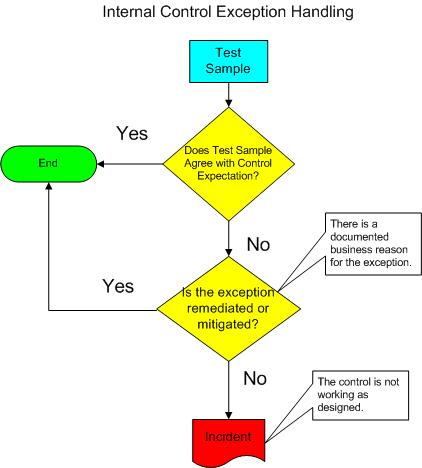
Control Commentary
Insert a description of the control that is applicable to the existing control statement this commentary refers to.
Control Exception Commentary
Insert a description of the control exception that is applicable to the existing control statement this commentary refers to.
Evidence Archive Location
Insert Evidence Description Here.
Control Status and Auditors Commentary
Describe the condition of the applicable control and its effectiveness. Set the color icon to a redlock.jpg, yellowlock.jpg or greenlock.jpg.
File:Redlock.jpg
Remediation Plan
Insert remediation plan, applicability, or any information that indicates what needs to be done.
Supplemental Information:
ITIL Security Management.
ITIL Security Management Measures.
ITIL 4.3 Audit and evaluate security reviews of IT systems.
ISO 8.6 Media handling and security.
ISO 9.2 User access management.
Implementation guidance
Insert guidance in this section if it helps to elaborate upon the subject matter. Examples of evidence that would help guide the end user is desirable.